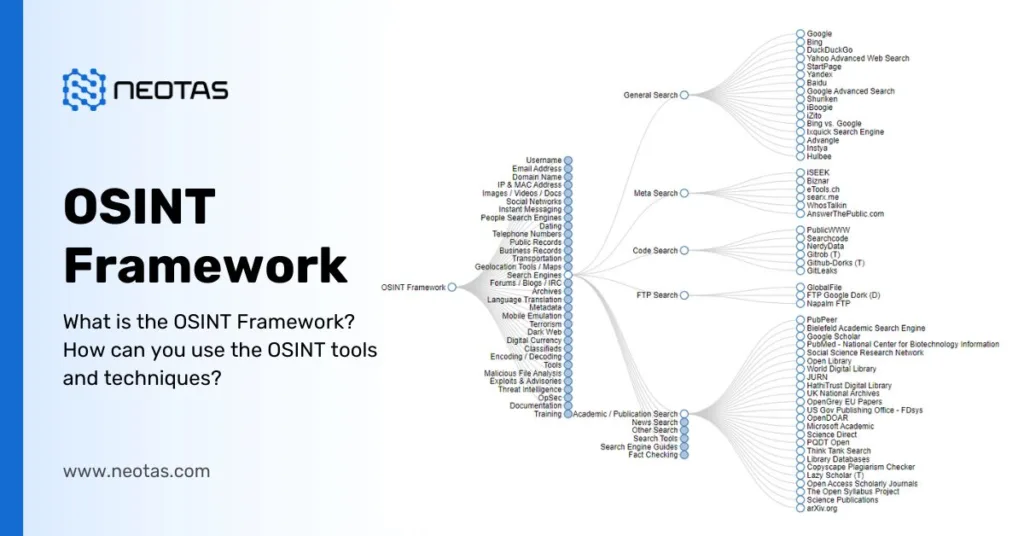
What is the OSINT Framework?
A Complete Guide to the OSINT Framework, Essential Tools, and Best Techniques – Explore How to use the OSINT framework.
OSINT, or Open Source Intelligence, refers to the practice of collecting, analysing, and leveraging information from publicly available sources to generate actionable intelligence.
OSINT is a methodology for gathering intelligence from open sources, which are publicly accessible sources of information. These sources can include traditional media (newspapers, magazines, TV, radio), publicly available data (government reports, commercial databases, social media), and the internet (websites, forums, blogs).
The OSINT (Open Source Intelligence) framework is a systematic approach to gathering, analysing, and leveraging publicly available information from various open sources. It provides a structured methodology for harnessing the vast amounts of data present in the digital landscape, enabling organisations, individuals, and researchers to gain valuable insights and intelligence.
OSINT Principles, Tools and Techniques:
The core principle of OSINT is to collect and analyse data that is freely available to the public, without resorting to covert or classified sources. This information can come from a wide range of sources, including:
- News and media outlets
- Social media platforms (Twitter, Facebook, LinkedIn, etc.)
- Online forums and discussion boards
- Company websites and public filings
- Government databases and public records
- Academic publications and research papers
- Geospatial data and satellite imagery
- Publicly available videos and podcasts
Advantages of using OSINT
The OSINT process involves systematically identifying, collecting, processing, and analysing these open-source data points to extract relevant intelligence.
This intelligence can then be used for various purposes, such as:
- Cybersecurity and threat intelligence
- Competitive intelligence and business analysis
- Law enforcement investigations
- National security and intelligence gathering
- Risk assessment and due diligence
- Journalism and research
OSINT is a critical component of modern intelligence gathering, as it provides a cost-effective and legal means of obtaining valuable information. It complements traditional intelligence sources and can be used to corroborate or supplement classified information.
The key advantage of OSINT is that it leverages publicly available data, which is often overlooked or underutilised. By employing advanced techniques and tools, OSINT professionals can extract insights and connections that may not be immediately apparent, enabling informed decision-making and strategic planning.
OSINT Framework
The OSINT framework is a comprehensive set of processes, techniques, and tools designed to facilitate the collection, processing, analysis, and dissemination of intelligence derived from publicly accessible sources. It encompasses a range of data sources, including the internet, social media platforms, public records, news reports, academic publications, and other open-source materials.
Importance of the OSINT framework
The OSINT (Open Source Intelligence) framework plays a crucial role in the modern intelligence landscape, and its importance cannot be overstated. Here are some key reasons why the OSINT framework is significant:
- Legal and ethical compliance: The OSINT framework operates within legal and ethical boundaries, as it relies on publicly available information. This mitigates the risks associated with unauthorised access or illegal data collection, ensuring compliance with relevant laws and regulations.
- Comprehensive intelligence gathering: The OSINT framework enables the collection and analysis of information from a wide range of open sources, providing a comprehensive view of the intelligence landscape. This approach can uncover insights and connections that may not be apparent from a single source, leading to more informed decision-making.
- Corroboration and verification: OSINT can be used to corroborate or verify information obtained from other sources, including classified or covert intelligence. By cross-referencing multiple open sources, analysts can validate the accuracy and reliability of intelligence, enhancing its credibility and usefulness.
- Proactive intelligence: The OSINT framework allows for proactive intelligence gathering, enabling organisations to anticipate and respond to potential threats, risks, or opportunities before they materialise. By monitoring open sources continuously, analysts can identify emerging trends, patterns, and indicators, facilitating early warning and prevention strategies.
- Support for various domains: The versatility of the OSINT framework makes it applicable to a wide range of domains, including cybersecurity, law enforcement, business intelligence, national security, journalism, and academic research. This versatility ensures that the framework remains relevant and valuable across diverse industries and sectors.
- Transparency and accountability: By relying on publicly available information, the OSINT framework promotes transparency and accountability in intelligence gathering. This approach allows for independent verification and oversight, fostering trust and credibility in the intelligence process.
- Continuous adaptation: The OSINT framework is dynamic and adaptable, allowing for the incorporation of new tools, techniques, and methodologies as the open-source landscape evolves. This adaptability ensures that the framework remains relevant and effective in the face of technological advancements and changing information landscapes.
- Cost-effectiveness: Gathering intelligence from open sources is generally more cost-effective than relying solely on classified or covert methods. The OSINT framework leverages publicly available data, which can be accessed and analysed at a relatively low cost, making it a viable option for organisations with limited resources.
The OSINT framework provides a structured and effective approach to leveraging the vast amounts of publicly available data for intelligence purposes. Its importance lies in its cost-effectiveness, legal compliance, comprehensiveness, corroboration capabilities, proactive nature, versatility, transparency, and adaptability, making it an indispensable tool in the modern intelligence ecosystem.
How to use the OSINT framework?
The OSINT (Open Source Intelligence) framework provides a structured approach to gathering and analysing intelligence from publicly available sources. Here’s a general outline of how to effectively use the OSINT framework:
- Define the Intelligence Requirements: Start by clearly defining the intelligence requirements or objectives. Identify the specific information or insights you need to gather, and determine the scope and focus of your OSINT efforts.
- Identify Relevant Sources: Based on your intelligence requirements, identify the most relevant open sources that may contain valuable information. These can include news websites, social media platforms, public databases, government publications, online forums, and more.
- Develop a Collection Plan: Create a systematic plan for collecting data from the identified sources. This may involve setting up web monitoring tools, creating search queries, subscribing to relevant feeds or alerts, and establishing a schedule for data collection.
- Data Collection: Implement your collection plan and begin gathering data from the identified open sources. Ensure that you adhere to legal and ethical guidelines, respecting intellectual property rights and privacy considerations.
- Data Processing and Organisation: As data is collected, process and organise it in a structured manner. This may involve creating databases, tagging or categorising information, and removing duplicates or irrelevant data.
- Data Analysis: Apply analytical techniques to extract insights and intelligence from the collected data. This can involve identifying patterns, trends, connections, and anomalies. Use appropriate tools and techniques, such as data visualisation, link analysis, sentiment analysis, or geospatial analysis, depending on your objectives.
- Validation and Corroboration: Validate and corroborate the findings by cross-referencing multiple open sources and verifying the information through additional research or subject matter expertise.
- Reporting and Dissemination: Present the intelligence findings in a clear and concise manner, using appropriate reporting formats and visualisation techniques. Disseminate the intelligence to relevant stakeholders or decision-makers.
- Continuous Monitoring and Feedback: Continuously monitor open sources for new or updated information that may impact your intelligence requirements. Incorporate feedback and lessons learned to refine and improve your OSINT processes.
- Ethical and Legal Compliance: Ensure that all OSINT activities are conducted in compliance with applicable laws, regulations, and ethical guidelines. Respect privacy, intellectual property rights, and avoid any unauthorised access or illegal data collection practices.
It’s important to note that the OSINT framework is iterative and may require adjustments based on the specific intelligence requirements, available resources, and evolving open-source landscape. Additionally, it’s often beneficial to integrate OSINT with other intelligence sources and methodologies to obtain a comprehensive understanding of the intelligence picture.
Advanced Techniques in OSINT Framework
Let’s dive deeper into some of the advanced OSINT techniques:
Web Data Scraping:
- Advanced Scraping Frameworks: Tools like Scrapy (Python) and Apify provide advanced scraping capabilities, including handling JavaScript-rendered content, rotating proxies, and scaling scraping operations across multiple machines.
- Headless Browsing: Headless browsers like Puppeteer (Node.js) and Selenium allow scraping dynamic and AJAX-heavy websites by rendering JavaScript and interacting with webpages like a real user.
- Data Extraction and Parsing: Advanced techniques involve using machine learning models for intelligent data extraction, such as named entity recognition (NER) and optical character recognition (OCR) for extracting text from images and PDFs.
Social Media Intelligence (SOCMINT):
- Advanced Social Media Monitoring: Tools like Brandwatch, Crimson Hexagon, and Synthesio enable comprehensive social media monitoring across multiple platforms, providing sentiment analysis, influencer identification, and trend detection capabilities.
- Network Analysis: Network analysis tools like Gephi and NodeXL can be used to visualise and analyse social networks, identify key influencers, detect communities, and uncover hidden connections between individuals or groups.
- Natural Language Processing (NLP): NLP techniques, such as topic modeling, sentiment analysis, and named entity recognition, can be applied to social media data to extract valuable insights, detect trends, and identify potential threats or risks.
Dark Web Monitoring:
- Automated Crawlers and Scrapers: Tools like Tor Project’s Stem library and Scrapy-Splash allow automating the crawling and scraping of dark web content, enabling large-scale data collection and analysis.
- Virtual Environments and Sandboxing: Virtual machines, containers, and sandboxing techniques are used to safely access and analyse dark web content, isolating potential threats and maintaining operational security.
- Cryptocurrency Transaction Monitoring: Blockchain analysis tools like Chainalysis and Elliptic can be used to monitor and trace cryptocurrency transactions, potentially uncovering illicit activities and connections on the dark web.
Geospatial Intelligence (GEOINT):
- Remote Sensing and Satellite Imagery Analysis: Advanced techniques involve using remote sensing data from sources like Landsat, Sentinel, and commercial providers, combined with machine learning algorithms for object detection, change detection, and pattern recognition.
- 3D Modeling and Visualisation: Tools like ArcGIS Pro and ENVI can be used to create 3D models and visualisations of geographic areas, enabling detailed analysis of terrain, infrastructure, and activities.
- Geospatial Data Integration: Integrating various geospatial data sources, such as satellite imagery, aerial photographs, terrain data, and GIS data, can provide a comprehensive understanding of an area of interest.
Network Traffic Analysis:
- Deep Packet Inspection (DPI): DPI techniques involve inspecting the data portion of network packets, allowing for detailed analysis of network traffic, detecting malicious activities, and extracting intelligence from encrypted traffic.
- Network Behavior Analysis: Tools like Zeek (formerly Bro) and Suricata can be used to analyse network traffic patterns, detect anomalies, and uncover potential threats or intelligence based on network behavior.
- Network Flow Analysis: Network flow analysis tools like SiLK and Argus can be used to analyse network flow data, providing insights into communication patterns, bandwidth usage, and potential security incidents.
Digital Forensics:
- Memory Forensics: Tools like Volatility and Rekall can be used to analyse and extract data from system memory dumps, enabling the recovery of encrypted data, deleted files, and other valuable forensic artifacts.
- Disk and File System Forensics: Advanced techniques involve using tools like The Sleuth Kit, EnCase, and FTK to perform in-depth analysis of disk images and file systems, recovering deleted data, analysing metadata, and uncovering digital evidence.
- Malware Analysis: Sandboxing tools like Cuckoo Sandbox and Joe Sandbox can be used for dynamic malware analysis, enabling the controlled execution and monitoring of malicious code to understand its behavior and functionality.
Machine Learning and Artificial Intelligence:
- Natural Language Processing (NLP): NLP techniques like named entity recognition, sentiment analysis, and topic modeling can be applied to large text datasets to extract valuable intelligence and insights.
- Computer Vision and Image Recognition: Machine learning models can be trained to analyse and classify images, detect objects, and identify patterns or anomalies in visual data.
- Predictive Analytics and Anomaly Detection: Techniques like clustering, regression, and anomaly detection algorithms can be used to identify patterns, forecast future events, and detect deviations or potential threats within large datasets.
Data Visualisation and Link Analysis:
- Interactive Data Visualisation: Tools like Tableau, Power BI, and D3.js enable the creation of interactive and dynamic visualisations, allowing analysts to explore and present data in intuitive and insightful ways.
- Link Analysis and Graph Visualisation: Tools like Neo4j, Gephi, and Palantir enable link analysis and graph visualisation, helping analysts uncover hidden connections, identify key nodes, and understand complex relationships within large datasets.
- Geospatial Data Visualisation: GIS software like ArcGIS and QGIS can be used to visualise and analyse geospatial data, enabling the creation of interactive maps, overlaying multiple data sources, and identifying spatial patterns and trends.
These advanced OSINT techniques often require specialised skills, tools, and resources, as well as a deep understanding of data analysis, programming, and domain-specific knowledge. They are typically employed by intelligence agencies, law enforcement, cybersecurity professionals, and researchers to gather intelligence, uncover threats, and gain a deeper understanding of complex situations or phenomena.
Applying the OSINT Framework
The OSINT (Open Source Intelligence) framework and the intelligence cycle are closely intertwined, providing a structured approach to gathering and analysing intelligence from publicly available sources. Applying the OSINT framework effectively involves adhering to the stages of the intelligence cycle, which ensures a systematic and comprehensive process for generating actionable intelligence.
OSINT lifecycle
The OSINT lifecycle encompasses the following stages:
- Planning and Direction: This initial stage involves defining the intelligence requirements, objectives, and priorities. It involves understanding the specific information needs, identifying relevant sources, and developing a collection plan tailored to the intelligence requirements.
- Collection: During this stage, analysts employ various techniques to gather data from open sources. This includes leveraging advanced search operators, web scraping tools, and analysing IP addresses to identify potential threats and uncover detailed information about industrial equipment, vulnerabilities, and security incidents related to industrial control systems.
- Processing and Exploitation: Collected data is processed, organised, and transformed into a format suitable for analysis. This may involve data cleaning, normalisation, and enrichment techniques, as well as the integration of data from multiple sources.
- Analysis and Production: In this stage, analysts apply various analytical techniques to extract insights and intelligence from the processed data. This includes the analysis of documents like patent filings, technical manuals, industry reports, and other relevant sources. Data analysis tools, such as data visualisation, link analysis, and machine learning algorithms, are instrumental in identifying trends, vulnerabilities, and operational insights about industrial control systems.
- Dissemination: The final stage involves presenting the intelligence findings in a clear and concise manner, tailored to the specific audience or decision-makers. This may involve the creation of reports, briefings, or interactive dashboards, ensuring that the intelligence is accessible and actionable.
Throughout the OSINT lifecycle, it is crucial to maintain a feedback loop, continually refining and adapting the process based on new intelligence requirements, emerging threats, or changing operational environments.
By seamlessly integrating the OSINT framework with the intelligence cycle, analysts can leverage the vast array of publicly available information to generate comprehensive and actionable intelligence. This intelligence can inform decision-making processes, support risk mitigation strategies, and enhance the security and resilience of industrial control systems and critical infrastructure.
Furthermore, combining OSINT techniques with traditional intelligence gathering methods can provide a more holistic and well-rounded intelligence picture, enabling organisations to stay ahead of potential threats and make informed decisions to safeguard their operations and assets.
OSINT industries – Open Source Intelligence for Various Sectors
Open Source Intelligence (OSINT) can be applied across various sectors to gather valuable intelligence, insights, and data from publicly available sources, supporting informed decision-making, risk management, and strategic planning. Here are some industries and use cases for Open Source Intelligence (OSINT):
- National Security and Intelligence Agencies:
- Monitoring online activities, social media, and public forums for potential threats, extremist activities, or terrorism-related information.
- Gathering intelligence on foreign governments, organisations, and individuals of interest from open sources.
- Analysing publicly available data to identify patterns, connections, and potential security risks.
- Financial Services and Investment Firms:
- Conducting due diligence on potential investments, mergers, acquisitions, or partnerships using public data sources.
- Monitoring news, social media, and online forums for information that could impact financial markets, stocks, or investment decisions.
- Gathering competitive intelligence and insights into industry trends and customer sentiment.
- Human Resources and Talent Acquisition:
- Conducting background checks and screening potential candidates using publicly available information.
- Monitoring social media profiles and online activities of candidates to assess cultural fit and potential risks.
- Gathering insights into industry trends, skills in demand, and talent market dynamics.
- Supply Chain and Logistics:
- Monitoring news, social media, and online forums for potential disruptions, natural disasters, or events that could impact supply chain operations.
- Gathering intelligence on suppliers, vendors, and partners to assess risks and compliance.
- Analysing public data sources for insights into consumer demand, market trends, and logistics optimisation.
- Real Estate and Urban Planning:
- Gathering data from public sources on demographics, market trends, and community sentiment for location analysis and property development.
- Monitoring online forums, social media, and news for information on zoning regulations, infrastructure projects, and local events that could impact real estate decisions.
- Analysing public data sources for insights into housing market dynamics, property values, and consumer preferences.
- Healthcare and Pharmaceutical Industries:
- Monitoring online forums, social media, and patient communities for information on drug side effects, treatment experiences, and consumer sentiment.
- Gathering intelligence on emerging health trends, disease outbreaks, or public health concerns from public data sources.
- Analysing public data to identify potential target populations, market opportunities, or areas for research and development.
- Cybersecurity:
- Identifying potential threats, vulnerabilities, and attack vectors by monitoring online forums, social media, and hacker communities.
- Gathering information about threat actors, their techniques, and motivations.
- Analysing publicly available data breaches and leaks for potential impact and risk assessment.
- Business Intelligence and Competitive Analysis:
- Monitoring competitors’ activities, strategies, and product launches through their websites, press releases, and social media presence.
- Tracking industry trends, market dynamics, and customer sentiment by analysing online forums, reviews, and social media discussions.
- Gathering information about potential business partners, suppliers, or acquisition targets from public sources.
- Law Enforcement and Criminal Investigations:
- Gathering intelligence about criminal organisations, their activities, and members from online sources.
- Monitoring social media platforms and public forums for potential threats, illegal activities, or suspicious behavior.
- Analysing publicly available data to identify patterns, connections, and potential leads in investigations.
- Risk Management and Due Diligence:
- Conducting background checks on individuals, companies, or organisations using publicly available information.
- Assessing potential risks associated with business deals, partnerships, or investments by analysing online sources.
- Monitoring news, social media, and other public sources for emerging risks or issues that could impact operations or reputation.
- Marketing and Brand Reputation Management:
- Monitoring social media platforms, online forums, and review sites for customer feedback, sentiment, and brand perception.
- Analysing online trends, influencers, and conversations relevant to the brand or industry.
- Gathering insights into target audiences, their interests, and behavior from publicly available data sources.
- Journalism and Research:
- Gathering information from various online sources, including government databases, social media, and public records.
- Verifying and corroborating information from multiple open sources for investigative reporting or academic research.
- Monitoring online discussions and trends related to specific topics or areas of interest.
Read more on Risk Management and Due Diligence: Due Diligence Explained: Types, Checklist, Process, Reports
What is the OSINT framework?
Key takeaways
The OSINT Framework: A Structured Approach to Open-Source Intelligence
The OSINT Framework provides a systematic and comprehensive methodology for leveraging publicly available information in the ever-expanding digital landscape. It offers a robust set of tools and techniques tailored to effectively gather, process, and analyse open-source data, enabling organisations to gain valuable insights and actionable intelligence.
OSINT Tools: Harnessing the Power of Online Data
Within the OSINT Framework, a suite of powerful tools facilitate efficient data harvesting from a multitude of online sources, including social media platforms, search engines, and the deep and dark web. These tools empower analysts to uncover critical information across diverse sectors, ranging from cybersecurity and competitive intelligence to investigative journalism and academic research.
Ethical Considerations: Upholding Principles and Compliance
Ethical considerations are paramount in the realm of OSINT gathering. As a thought leader, I firmly believe in adhering to legal standards such as the General Data Protection Regulation (GDPR) and ensuring the ethical collection of data. Respecting terms of service, maintaining transparency, and safeguarding individual privacy are fundamental principles that must be upheld throughout the OSINT process.
Unlocking Insights with OSINT
The OSINT Framework provides a robust and versatile approach to unlocking invaluable insights from the vast expanse of publicly available information. By embracing a structured methodology, leveraging cutting-edge tools, and upholding ethical standards, organizations can navigate the complexities of the digital landscape and gain a competitive edge in their respective domains.
FAQs on OSINT Framework
What is the OSINT framework?
The OSINT (Open Source Intelligence) framework is a comprehensive methodology for gathering, processing, analysing, and leveraging intelligence from publicly available sources. It provides a structured approach to identifying relevant open sources, collecting data, extracting insights, and disseminating actionable intelligence. The framework encompasses various stages, including planning, collection, processing, analysis, and reporting, allowing for a systematic and repeatable process. It is widely adopted by intelligence agencies, law enforcement, cybersecurity professionals, and researchers to complement traditional intelligence sources.
What are the 5 steps of OSINT?
The five main steps of the OSINT process within the intelligence cycle are:
- Planning and Direction: Defining intelligence requirements, objectives, and identifying relevant open sources.
- Collection: Gathering data from identified open sources using various techniques and tools.
- Processing and Exploitation: Organising, cleaning, and transforming collected data into a usable format.
- Analysis and Production: Applying analytical methods to extract insights, identify patterns, and generate intelligence products.
- Dissemination: Presenting the intelligence findings in a clear and actionable manner to relevant stakeholders or decision-makers.
What are OSINT tools used for?
OSINT tools are used for various purposes, including:
- Data collection from online sources like websites, social media platforms, forums, and databases.
- Processing and organising large amounts of collected data for analysis.
- Identifying patterns, trends, and connections within the data through advanced analytical techniques.
- Monitoring and tracking changes or updates in relevant open sources.
- Visualising and presenting intelligence findings in an understandable and impactful manner.
Is OSINT legal?
Yes, OSINT is generally considered legal as it involves collecting and analysing information from publicly available sources. However, it is crucial to adhere to legal and ethical guidelines, respect intellectual property rights, and avoid any unauthorised access or illegal data collection practices. Ethical considerations, such as privacy protection and transparency, are also essential when conducting OSINT activities.
What are the 3 pillars of OSINT?
The three pillars of OSINT are:
- Legal and Ethical Compliance: Ensuring that OSINT activities comply with applicable laws, regulations, and ethical standards, respecting privacy and intellectual property rights.
- Transparency: Promoting transparency in OSINT processes, methodologies, and the use of publicly available data, fostering trust and accountability.
- Adaptability: Being adaptable to evolving data landscapes, incorporating new tools, techniques, and methodologies to stay relevant and effective in the face of technological advancements and changing information environments.
Is Google an OSINT tool?
Yes, Google can be considered an OSINT tool as it enables searching and accessing a vast amount of publicly available information on the internet. Google’s search capabilities, combined with advanced search operators and techniques, make it a valuable resource for OSINT practitioners to gather relevant data from various online sources, including websites, news articles, social media, and public databases.
How do I get into OSINT?
To get into the field of OSINT, you can follow these steps:
- Learn the fundamentals of OSINT techniques, methodologies, and tools through online resources, courses, or training programs offered by reputable institutions or organisations.
- Develop essential skills such as critical thinking, data analysis, research, and problem-solving.
- Gain hands-on experience by practicing OSINT techniques on various open sources and participating in online OSINT communities or projects.
- Consider pursuing certifications or qualifications in OSINT, cybersecurity, or related fields to demonstrate your knowledge and expertise.
- Build a portfolio of OSINT projects or case studies to showcase your skills and accomplishments.
- Network with professionals in the OSINT industry, attend conferences or meetups, and explore job opportunities in relevant sectors like intelligence agencies, law enforcement, cybersecurity firms, or research organisations.
What is an example of OSINT?
Examples of OSINT activities include:
- Gathering intelligence from news articles, social media posts, online forums, and public databases.
- Monitoring and analysing online discussions, trends, and sentiment related to specific topics or events.
- Leveraging search engines, web crawlers, and scraping tools to collect data from websites and online sources.
- Analysing publicly available satellite imagery, maps, and geographic data for geospatial intelligence (GEOINT).
- Investigating public records, company filings, and patent databases for competitive intelligence or due diligence purposes.
- Tracking and monitoring online activities, websites, and social media profiles related to potential threats or subjects of interest.
Is it safe to use OSINT?
OSINT can be considered safe when conducted legally and ethically, respecting privacy and intellectual property rights. However, it is important to exercise caution and follow best practices to mitigate potential risks:
- Adhere to applicable laws and regulations related to data collection, privacy, and intellectual property.
- Respect the terms of service and usage policies of online platforms and sources.
- Avoid any unauthorised access, hacking, or illegal data collection practices.
- Implement appropriate security measures to protect your own systems and data during OSINT activities.
- Be aware of the potential for inadvertently collecting or exposing sensitive or personal information.
- Maintain transparency and accountability in your OSINT processes and methodologies.
What is the dark side of OSINT?
The “dark side” of OSINT refers to the potential misuse of open-source intelligence techniques and tools for illegal, unethical, or malicious purposes. This can include:
- Gathering intelligence for cyber attacks, cybercrime, or other malicious activities.
- Conducting unauthorised surveillance or infringing on privacy rights.
- Engaging in corporate espionage, stealing trade secrets, or violating intellectual property rights.
- Spreading misinformation, disinformation, or propaganda through open sources.
- Exploiting vulnerabilities or sensitive information obtained through OSINT for nefarious purposes.
- Engaging in unethical or illegal data collection practices, such as scraping without authorisation or violating terms of service.
Is OSINT really intelligence?
Yes, OSINT (Open Source Intelligence) is considered a legitimate and valuable source of intelligence when gathered, processed, and analysed systematically using established methodologies and techniques. OSINT provides insights, context, and corroboration to support decision-making processes, inform risk assessments, and complement other intelligence sources. While OSINT relies on publicly available information, the intelligence value lies in the ability to collect, analyse, and interpret this data in a structured and meaningful way to generate actionable intelligence products.
Is OSINT well paid?
OSINT professionals can be well compensated, particularly in industries and sectors that heavily rely on open-source intelligence, such as:
- Cybersecurity and threat intelligence: OSINT analysts play a crucial role in identifying potential threats, vulnerabilities, and cyber risks, commanding competitive salaries in this high-demand field.
- National security and intelligence agencies: Government agencies responsible for national security and intelligence operations often employ OSINT professionals and offer competitive compensation packages.
- Competitive intelligence and business analytics: Companies in various industries utilise OSINT for competitive analysis, market research, and strategic decision-making, leading to well-paying opportunities for skilled OSINT professionals.
- Law enforcement and investigative agencies: OSINT techniques are valuable in supporting investigations, forensics, and intelligence gathering for law enforcement agencies, which can offer lucrative career paths.
Factors such as education, certifications, experience, and specialised skills can further influence earning potential in the OSINT field.
Is OSINT passive or active?
OSINT can be both passive and active:
Passive OSINT involves collecting and analysing publicly available information without directly interacting with sources or individuals. Examples of passive OSINT include:
- Searching and gathering data from online sources like websites, social media platforms, and public databases.
- Analysing satellite imagery, maps, and other geospatial data.
- Reviewing publicly available documents, reports, and media publications.
Active OSINT involves directly engaging with sources, communities, or individuals to gather information. Examples of active OSINT include:
- Participating in online forums, discussion boards, or social media groups related to topics of interest.
- Conducting interviews, surveys, or eliciting information from individuals or subject matter experts.
- Attending conferences, events, or public meetings to gather intelligence through observation and interaction.
Both passive and active OSINT techniques can be employed, depending on the specific intelligence requirements, objectives, and ethical considerations.
What is the difference between PAI and OSINT?
PAI (Publicly Available Information) and OSINT (Open Source Intelligence) are related but distinct concepts:
PAI refers to the data or information itself that is publicly available and accessible from open sources. This can include websites, social media platforms, news articles, public records, databases, and other publicly accessible sources.
OSINT, on the other hand, encompasses the processes, techniques, and methodologies used to collect, process, analyse, and leverage PAI to generate actionable intelligence. OSINT involves the systematic and structured gathering, evaluation, and interpretation of publicly available information to support decision-making, risk assessment, and intelligence operations.
In essence, PAI is the raw data or information that exists in the public domain, while OSINT is the practice of transforming that data into valuable intelligence through various analytical techniques and frameworks.
What are the top four obstacles to effectively using OSINT?
The top four obstacles to effectively using OSINT are:
- Information overload: The sheer volume of publicly available data from various online sources can be overwhelming, making it challenging to identify relevant and reliable information.
- Verifying source credibility: Assessing the credibility and trustworthiness of information sources is crucial in OSINT, as open sources can contain inaccuracies, biases, or disinformation.
- Legal and ethical constraints: OSINT practitioners must navigate legal and ethical boundaries, respect privacy and intellectual property rights, and adhere to relevant regulations and policies.
- Rapidly evolving data landscapes: The constant evolution of online platforms, data formats, and technologies necessitates continuous adaptation and the development of new OSINT techniques and tools.
Other obstacles may include limited access to certain data sources, language barriers, resource constraints, and the potential for adversaries to obfuscate or manipulate open-source information.
Manage Business Risk with OSINT.
Neotas is an Enhanced Due Diligence Platform that leverages AI to join the dots between Corporate Records, Adverse Media and Open Source Intelligence (OSINT).
Schedule a Call or Book a Demo of Neotas Enhanced Due Diligence Platform.
Read More about Open Source Intelligence:
- OSINT Framework, OSINT Tools, OSINT Techniques, and how to use OSINT framework.
- Open Source Intelligence (OSINT) in the Fight Against Financial Crime
- Reduce & Manage Business Risk with Neotas Open Source Intelligence (OSINT) Solutions
- Open Source Intelligence (OSINT) based AML Solution sees beneath the surface
- Enhancing ESG Risk Management Framework with Neotas’ OSINT Integration
- How Open Source Intelligence (OSINT) is transforming enhanced due diligence and investigations in AML compliance
- Detecting Modern Slavery In Your Supply Chain using Open-source Intelligence
- Creating an effective framework for managing risk with suppliers and third parties using open-source intelligence (OSINT)
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation
- Risk-Based Approach (RBA) to AML & KYC risk management
- Anti-Money Laundering (AML)
- Supply Chain Risk Management
- Using Open Source Intelligence For Enhanced Due Diligence


 Financial Crime Compliance Trends 2024
Financial Crime Compliance Trends 2024












