What is Third-Party Risk Management (TPRM)?
Navigating Third-Party Risk Management in the UK
Third-Party Risk Management (TPRM) has evolved from a periodic compliance task into a critical daily function for organisations. In this comprehensive guide, we demystify TPRM, elucidate its driving forces, and underscore the paramount importance of its implementation.
Implementing a Third-Party Risk Management initiative empowers businesses to proactively identify and mitigate risks associated with external partnerships.
Third-Party Risk Management is also known as ‘vendor risk management’, ‘supply chain risk management’, or ‘supplier risk management’, stands as a vital subset within the broader domain of risk management.
TPRM Meaning
TPRM entails the meticulous assessment and mitigation of risks associated with outsourcing to third-party vendors or service providers. These encompass a spectrum of digital risks, spanning financial, environmental, reputational, and security concerns.
The crux lies in recognising that vendors possess access to invaluable assets such as intellectual property, sensitive data, including Personally Identifiable Information (PII) and Protected Health Information (PHI). Given the indispensable nature of third-party relationships in business operations, Third-Party Risk Management forms an integral facet of all robust Cybersecurity programmes.
Third-party risk management services play a pivotal role in enhancing a company’s understanding of its operational landscape. These services enable businesses to:
- Identify and list the third-party vendors in their network, ensuring transparency and accountability.
- Implement predictive measures to assess the stability risks associated with crucial customers, business partners, and vendors, thereby preemptively addressing potential disruptions.
- Analyse the methods and extent of engagement with third parties, offering insight into the inherent risk profiles and facilitating informed decision-making.
- Evaluate the efficacy of existing risk identification and reduction practices, ensuring a robust and adaptive risk management framework.
What is Third-Party Risk?
At its core, third-party risk revolves around the potential for an originating organisation to suffer a data breach or face detrimental consequences through affiliations with external entities. Common third parties comprise suppliers, vendors, partners, service providers, and contractors, all privy to privileged information, including customer data and internal processes.
Why is Third-Party Risk Management (TPRM) Important?
In today’s interconnected business landscape, third-party risk management has emerged as a critical discipline. The escalating reliance on outsourcing coupled with a surge in breaches across industries has propelled TPRM to the forefront of business strategies. Disruptive events, regardless of an organisation’s size, location, or industry, have underscored the imperative need for robust Third-Party Risk Management practices.
In this article, we will delve into the profound significance of Third-Party Risk Management and how it safeguards businesses from a multitude of potential threats.
Navigating Operational Vulnerabilities
- Internal Outages and Operational Lapses: Third-Party Risk Management plays a pivotal role in mitigating internal disruptions and operational shortcomings. Ensuring the continuity of essential services within an organisation relies heavily on the reliability of third-party service providers. In the absence of a robust TPRM framework, internal functions may grind to a halt, potentially leading to significant financial losses and reputational damage.
- External Supply Chain Outages: The modern supply chain is a complex web of interdependent entities. Any disruption in the supply chain, whether due to unforeseen events or failures within third-party components, can have a cascading effect on an organisation’s ability to deliver products or services. Effective Third-Party Risk Management acts as a bulwark against such external shocks, enabling businesses to navigate through disruptions with resilience.
- Vendor-Induced Vulnerabilities: Entrusting critical operations to vendors introduces a degree of vulnerability to an organisation. Inadequate controls or disruptions within a vendor’s operations can expose an organisation to unforeseen risks. A robust Third-Party Risk Management program ensures that vendors adhere to stringent security measures, mitigating potential supply chain vulnerabilities.
Securing Data Integrity and Confidentiality
- Cybersecurity Posture: Engaging third parties amplifies the complexity of an organisation’s information security landscape. While outsourcing to specialists is often a prudent business decision, it necessitates vigilant risk management. Third-Party Risk Management acknowledges that third parties operate outside an organisation’s immediate sphere of control, urging stringent assessments and vigilance.
- Transparency and Security Controls: Unlike internal operations, third parties operate with a level of autonomy. This lack of direct oversight mandates a comprehensive understanding of a vendor’s security controls. A robust Third-Party Risk Management program discerns vendors with rigorous security standards from those with gaps, ensuring that only trusted partners are integrated into the business ecosystem.
- Minimising Attack Vectors: Each third-party engagement introduces a potential pathway for cyber threats. The larger the network of vendors, the broader the attack surface. A diligent Third-Party Risk Management approach evaluates and mitigates these risks, fortifying the organisation’s resilience against potential breaches or cyber attacks.
Compliance and Reputation Management
- Regulatory Impact: Evolving data protection and breach notification laws have heightened the regulatory and reputational stakes of inadequate Third-Party Risk Management. Entrusting third parties with sensitive information implicates an organisation in the event of a breach. A robust Third-Party Risk Management program ensures compliance with regulatory mandates, shielding the organisation from penalties and reputational harm.
What are the TPRM Best Practices?
Here are some TPRM best practices to help ensure an effective third-party risk management strategy. Let’s understand three critical best practices tailored to every business, regardless of their current Third-Party Risk Management maturity.
Prioritise Your Vendor Inventory
Distinguishing critical third parties from the rest is paramount. To streamline Third-Party Risk Management efficiency, categorise vendors into tiers based on their significance:
- Tier 3: Low risk, low criticality
- Tier 2: Medium risk, medium criticality
- Tier 1: High risk, high criticality
Tier 1 vendors necessitate meticulous due diligence, often involving on-site assessments. Calculated initially by inherent risk, factors like sharing sensitive data and critical business functions shape these tiers. Contract value can also influence tiering.
Leverage Automation for Efficiency
Automation stands as the linchpin of an effective TPRM strategy, ensuring consistency and repeatability. Areas ideal for automation include:
- Vendor onboarding: Streamline vendor addition through intake forms or integration with contract management systems.
- Risk assessment and tiering: Collect business context during onboarding to prioritise high-risk vendors.
- Task assignment: Route risks to the relevant stakeholders, along with mitigation checklists.
- Performance reviews: Automate yearly vendor reviews and trigger off-boarding for underperformers.
- Reassessment: Based on contract expiration, preserving previous assessments for continuity.
- Notifications and alerts: Integrate with existing systems to inform stakeholders of new risks or vendors.
- Report scheduling: Automatically generate and distribute reports on a regular basis.
Initiate automation by assessing repeatable internal processes, progressively implementing practical automations that yield significant time and resource savings.
Broaden Your Risk Horizon
While cybersecurity risks often dominate TPRM considerations, a comprehensive program encompasses a spectrum of risks beyond cybersecurity:
- Reputational risks
- Geographical risks
- Geopolitical risks
- Strategic risks
- Financial risks
- Operational risks
- Privacy risks
- Compliance risks
- Ethical risks
- Business continuity risks
- Performance risks
- Fourth-party risks
- Credit risks
- Environmental risks
Recognising these diverse risk facets is pivotal in crafting a world-class Third-Party Risk Management program.
Best Practices for TPRM Implementation
- Define Organisational Goals
Initiate TPRM by aligning identified risks with the organisation’s enterprise risk management framework. Establish a comprehensive inventory differentiating between third parties and their associated risk actions. Mature organisations map risks across various domains, including geopolitical, financial, reputational, compliance, privacy, and cyber risks.
- Gain Stakeholder Commitment
Effective TPRM hinges on stakeholder cooperation. Engage relevant parties early on, including risk, compliance, procurement, security, and commercial teams, to collectively shape and execute the TPRM program.
- Cultivate Partnerships with Business Units
Implement a robust monitoring strategy to assess third-party risks systematically. Regular assessments help identify and track high-risk parties, analyse the risk profile of the entire third-party portfolio, and evaluate major operational loss events.
- Implement Risk Tiering
Classify vendors into tiers based on criticality and risk levels. Focus initial efforts on Tier 1 vendors, conducting in-depth assessments to validate their security measures.
- Collaborate with Procurement
Incorporate procurement into the TPRM process, aligning third-party risk assessment with supplier evaluation. Evaluate high-risk exposure areas, considering geopolitical, financial, and natural disaster risks.
- Ensure Continuous Monitoring
Maintain vigilance through continuous monitoring, providing real-time insights into vendor risks. This proactive approach allows for swift response to changes in security posture.
By embracing these TPRM best practices, organisations fortify their resilience against an array of potential threats. From tiered vendor prioritisation to strategic automation and comprehensive risk consideration, these practices form the bedrock of a robust TPRM program.
Elevate your TPRM strategy to safeguard your business against evolving risks in today’s interconnected business landscape.
What is the Third-Party Risk Management Lifecycle?
The TPRM lifecycle encompasses a series of meticulously crafted stages that define a typical relationship with a third party. This article aims to provide a comprehensive insight into each phase, offering valuable guidance for businesses aiming to fortify their TPRM strategies.
Phase 1: Third-Party Identification
Identifying existing and potential third parties is the cornerstone of a robust TPRM program. Utilising existing data, integrating with current technologies, and conducting targeted assessments or interviews are crucial methods. A self-service portal empowers business owners to contribute vital information, facilitating preliminary risk evaluation. This data forms the basis for classifying third parties based on their inherent risk.
Phase 2: Evaluation and Selection
The evaluation and selection phase involves a meticulous consideration of Requests for Proposals (RFPs) and the subsequent choice of a vendor. This decision hinges on unique factors tailored to the business’s specific requirements.
Phase 3: Risk Assessment
Vendor risk assessments serve as the linchpin of TPRM, demanding time and resources. Many organisations leverage third-party risk exchanges or employ assessment automation software to streamline this process. Recognised standards like ISO 27001, NIST SP 800-53, and industry-specific benchmarks such as HITRUST guide this evaluation.
Phase 4: Risk Mitigation
Post-assessment, risks are identified, graded, and mitigation measures initiated. This involves flagging risks, evaluating their alignment with defined risk tolerance, and ensuring the implementation of necessary controls. Continuous monitoring is essential to track any events that may elevate risk levels.
Phase 5: Contracting and Procurement
The contracting and procurement stage, often concurrent with risk mitigation, holds pivotal significance in TPRM. While contracts contain multifaceted details, key provisions like scope of services, pricing, termination clauses, and data protection agreements should be closely scrutinised.
Phase 6: Reporting and Recordkeeping
Compliance maintenance is often overlooked but integral to a robust TPRM program. Auditable recordkeeping, facilitated by specialised TPRM software, streamlines reporting on critical program aspects. This ensures regulatory adherence and identifies areas for enhancement.
Phase 7: Ongoing Monitoring
TPRM extends beyond assessments, requiring vigilant, ongoing vendor monitoring. Evolving factors, such as regulatory changes, adverse publicity, data breaches, or shifts in vendor engagement, necessitate continuous vigilance. Monitoring key risk-altering events is crucial to adapt proactively.
Phase 8: Vendor Offboarding
Thorough offboarding procedures are vital for both security and regulatory compliance. An offboarding checklist, involving internal and external assessments, validates compliance with requisite measures. Maintaining an extensive evidence trail of these activities is crucial for audit readiness.
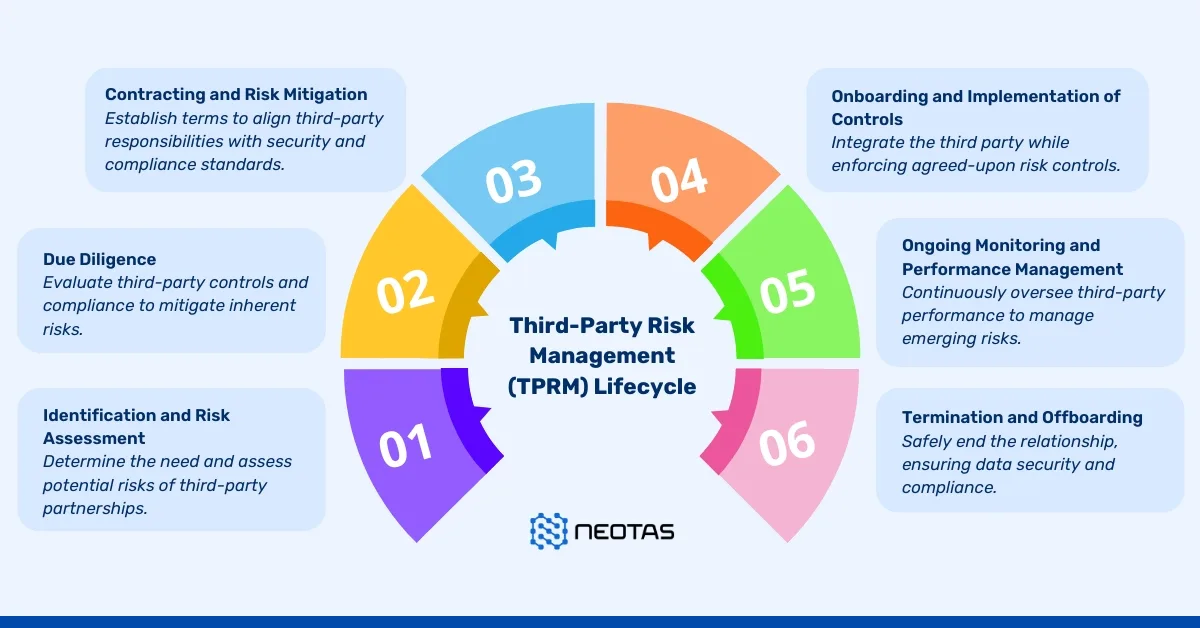
Beyond the Phases: TPRM Lifecycle Implementation
Incorporating the TPRM lifecycle into your organisation necessitates strategic planning and adaptable processes. These include:
- Sourcing and Selection: Evaluating vendors against baseline security, privacy, reputational, and financial risks via questionnaire-based assessments or vendor intelligence databases.
- Intake and Onboarding: Efficiently onboarding vendors into a central repository through intake forms, spreadsheet imports, or API integration with existing procurement solutions.
- Inherent Risk Scoring: Preliminary assessment of a vendor’s risk level before system access, determining subsequent due diligence requirements.
- Internal Controls Assessment: Periodic assessments to satisfy audit mandates, scoring risks based on impact, likelihood, and compliance with key frameworks like ISO, NIST, or SOC 2.
- External Risk Monitoring: Tapping into external intelligence sources for real-time third-party risk insights, validating assessment responses against external observations.
- SLA and Performance Management: Assessing vendor compliance with service level agreements, product performance, and responsiveness.
- Offboarding and Termination: Ensuring final obligations are met, including contract reviews, invoice settlement, system access revocation, and privacy/security compliance review.
Implementing Your TPRM Program
The success of Third-Party Risk Management (TPRM) program hinges on addressing critical questions that serve as the foundation for your program. In this guide, we will delve into these essential considerations and outline best practices to ensure a seamless implementation.
- Partnering for Success: Hiring a TPRM Expert
The decision to hire a partner for the implementation of your TPRM program can be instrumental in its success. An experienced partner can provide invaluable insights, streamline processes, and offer guidance on industry best practices. They bring a wealth of knowledge that can expedite the development and implementation of a robust TPRM framework.
- Managing Internal Stakeholder Expectations
Effectively managing the expectations of internal stakeholders is paramount. Clear communication regarding the objectives, benefits, and expected outcomes of the TPRM program is essential. Engaging key stakeholders early on and involving them in the decision-making process fosters a sense of ownership and ensures alignment with organisational goals.
- Assigning Responsibilities for Data Breach Scenarios
In the event of a data breach, having clearly defined responsibilities is crucial. Designate specific roles and responsibilities for incident response, communication, and remediation. This ensures a swift and coordinated response, minimising potential damage and protecting the interests of all parties involved.
- Defining Exact Requirements for Third Parties
Establishing precise requirements that third parties must meet to do business with your organisation is a foundational step. These requirements should encompass security standards, compliance obligations, data protection protocols, and performance benchmarks. Clarity in expectations lays the groundwork for a secure and mutually beneficial partnership.
- Ensuring Understanding and Implementation by External Stakeholders
Effective communication is key to ensuring that external stakeholders comprehend and can implement the established requirements. Provide comprehensive documentation, conduct training sessions, and establish channels for ongoing support and clarification. This proactive approach fosters compliance and strengthens the vendor’s ability to meet your organisation’s standards.
- Evaluating Financial Implications
Implementing TPRM requirements may impact the financial relationship with vendors. Consider conducting a thorough assessment to understand the potential cost implications. Strive for a balanced approach that aligns risk management objectives with the financial interests of both parties, seeking opportunities for mutual benefit.
- Rolling Out the Program in Existing Relationships
Integrating the TPRM program into existing vendor relationships requires a strategic approach. Begin by conducting a thorough assessment of current vendors, identifying areas that require immediate attention. Prioritise actions based on risk levels and establish a phased implementation plan, ensuring a smooth transition without disrupting critical operations.
Third-Party Vendor Risk Management
Third-Party Vendor Risk Management (TPVRM) refers to the processes and strategies organisations use to identify, assess, manage, and monitor risks associated with working with external vendors, suppliers, or service providers. As organisations increasingly rely on third-party entities for critical functions, effective risk management is essential to protect operational integrity, data security, and regulatory compliance.
Steps to Effective Vendor Risk Management
- Vendor Identification and Classification
- Create an inventory of all third-party vendors.
- Categorise vendors based on their criticality and the type of services provided.
- Risk Assessment
- Evaluate risks specific to each vendor, considering data sensitivity, operational dependence, and compliance requirements.
- Use questionnaires, audits, and risk scoring tools to gather insights.
- Due Diligence
- Assess vendors before onboarding, focusing on financial health, cybersecurity measures, and compliance track records.
- Contract Management
- Draft contracts that clearly define performance expectations, service levels, and security obligations.
- Include clauses for compliance, audits, and termination conditions.
- Continuous Monitoring
- Regularly monitor vendor performance, financial stability, and adherence to contractual terms.
- Employ tools like vendor management platforms for ongoing oversight.
- Incident Response and Contingency Planning
- Establish protocols for managing vendor-related incidents, such as data breaches or service disruptions.
- Develop backup plans for critical vendors to ensure business continuity.
Best Practices
- Adopt Technology Solutions: Use vendor management systems to centralise vendor data, automate assessments, and monitor risks.
- Engage Cross-Functional Teams: Involve legal, IT, procurement, and risk management teams in the process.
- Focus on Collaboration: Build strong relationships with vendors to encourage transparency and mutual risk mitigation.
- Stay Compliant: Align vendor risk processes with regulations such as GDPR, ISO 27001, or industry-specific standards.
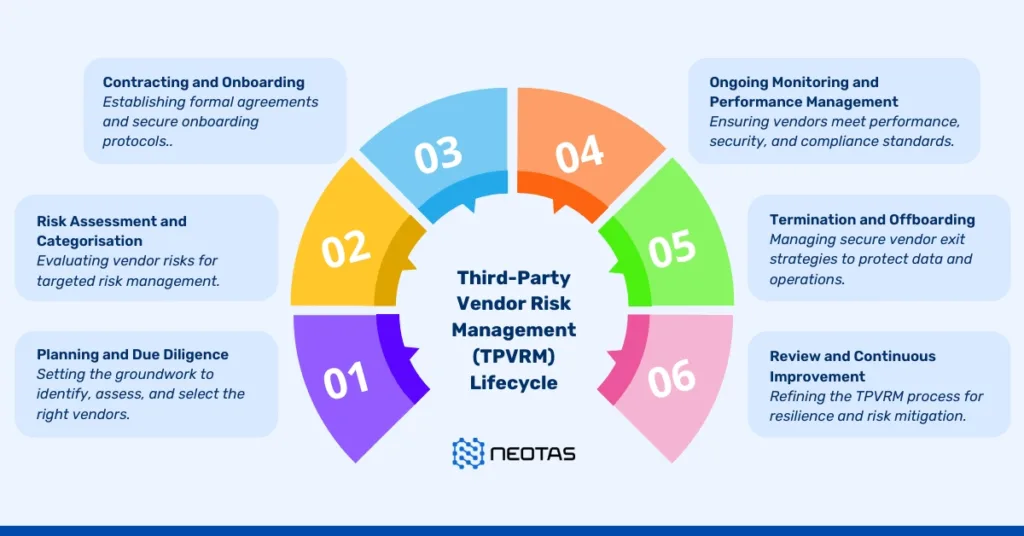
Third-party vendor risk management is critical for safeguarding an organisation’s operations, reputation, and compliance standing. By systematically identifying and addressing risks, organisations can establish secure and resilient vendor relationships that align with their strategic goals.
Third Party Business Risk Factors
Let’s delve into some common risk factors that businesses often face and how a strategic TPRM program can mitigate them.
- Reputational Risk Management
Maintaining a transparent and ethical business image is paramount. Effective third-party risk management helps in proactively addressing issues like forced labour, corruption, terrorist financing, and environmental impact. Leveraging a vendor risk management tool is a cost-effective way to minimise potential damage to your brand and corporate image. By staying vigilant, you can uphold your reputation and foster trust with stakeholders.
- Compliance Risks
The regulatory landscape is ever-evolving, making it crucial to stay vigilant and proactive in ensuring compliance. Third-party risk management tools provide real-time insights, allowing you to promptly adapt internal procedures and controls to align with changing regulations. By leveraging such tools, you can navigate the complexities of corporate compliance and sanctions risk effectively, safeguarding your business from legal repercussions.
- Financial Risk Management
Mitigating financial risks associated with fines, settlements, and remediation measures is imperative for preserving future business opportunities. Through daily monitoring of a vendor’s inherent risk, you can stay ahead of potential financial threats. By prioritising financial risk management within your TPRM program, you not only protect your business’s fiscal health but also ensure its long-term sustainability.
- Strategic Risk Management
Strategic third-party risk management is the cornerstone of a resilient TPRM program. By incorporating features that focus on Environmental, Social, and Governance (ESG) compliance and Corporate Social Responsibility (CSR), you create a robust framework. This approach allows you to identify lucrative opportunities within the supply chain and expand into new markets. Through strategic risk management, your business can proactively pursue growth and profitability.
Read about Third Party Risk Management and TPRM Lifecycle
How can Neotas TPRM solutions help?
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM). In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Moreover, Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
Want to benchmark your existing TPRM practices and get a roadmap to enhance your current TPRM practices?
If you’re curious about whether our third-party risk management solutions and services align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
Neotas Due Diligence Platform
FAQs on TPRM
What is third-party risk management?
Third-Party Risk Management is the systematic process of identifying, assessing, and mitigating potential risks associated with external partners, suppliers, or service providers. It ensures that these entities align with an organisation’s standards and regulatory requirements.
What is a third-party risk?
A third-party risk denotes the possible adverse effects that may result from the actions, policies, or performance of external entities, such as vendors, suppliers, or service providers, who have a business relationship with an organisation.
What is a third-party risk management process?
The third-party risk management process comprises distinct stages: identification, assessment, mitigation, monitoring, and response. This process systematically evaluates and addresses risks associated with external partners to safeguard the organisation’s interests.
How do you create a third-party risk management program?
Establishing a TPRM program necessitates defining its scope, objectives, and criteria for categorising third parties. This involves assessing risks, devising mitigation strategies, implementing monitoring protocols, and formulating response plans for potential incidents.
Who is responsible for third-party risk management?
Responsibility for TPRM is distributed among various stakeholders within an organisation, including senior management, compliance officers, procurement teams, legal departments, and information security professionals. Effective collaboration amongst these parties is pivotal for proficient TPRM.
What is the role of TPRM?
TPRM plays a vital role in shielding an organisation from potential risks associated with third-party relationships. By ensuring compliance with policies and regulations, it preserves the organisation’s reputation, financial stability, and operational continuity.
What is TPRM and why is it important?
TPRM, or Third-Party Risk Management, is crucial in identifying, assessing, and mitigating risks linked to external partners. It safeguards against financial loss, reputational damage, compliance breaches, and operational disruptions, thereby fortifying the organisation’s resilience.
What is the value of TPRM?
The value of TPRM lies in its capacity to enhance organisational resilience and security. It provides assurance that third parties meet requisite standards, diminishes the probability of adverse incidents, and upholds trust with stakeholders.
What is a TPRM framework?
A TPRM framework constitutes a structured approach outlining processes, procedures, and guidelines for managing third-party risks. It encompasses steps for identification, assessment, mitigation, monitoring, and response to risks pertaining to external partners.
What is TPRM assessment?
TPRM assessment entails evaluating the risks associated with third-party relationships. This includes examining factors such as compliance, financial stability, information security, and operational performance.
What is the TPRM process?
The TPRM process encompasses the steps involved in managing third-party risks, which include identification, assessment, mitigation, monitoring, and response.
What is the purpose of TPRM?
The purpose of TPRM is to safeguard an organisation from potential risks arising from its interactions with third parties. It ensures that third parties meet required standards, reducing the likelihood of negative incidents and protecting the organisation’s interests.
What are the functions of TPRM?
The functions of TPRM include:
- Identification and Categorisation of Third Parties: Recognising all external partners and classifying them based on risk.
- Risk Assessment: Evaluating the risks associated with each third party.
- Risk Mitigation: Implementing measures to reduce or manage identified risks.
- Ongoing Monitoring: Continuously overseeing third-party activities.
- Incident Response and Remediation: Developing plans for managing and responding to unforeseen issues or breaches.
What are the 5 phases of third-party risk management framework?
The five phases of TPRM encompass identification, assessment, mitigation, monitoring, and response. These stages collectively form a comprehensive approach to managing risks associated with external partners.
Related Case Studies:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation



 Financial Crime Compliance Trends 2024
Financial Crime Compliance Trends 2024












