Open Source Intelligence (OSINT)
Unlock the Benefits of Open Source Intelligence (OSINT) and Its Influence on Modern Investigatory Techniques. Learn how Open Source Intelligence software works, the OSINT framework, Techniques & Tools.
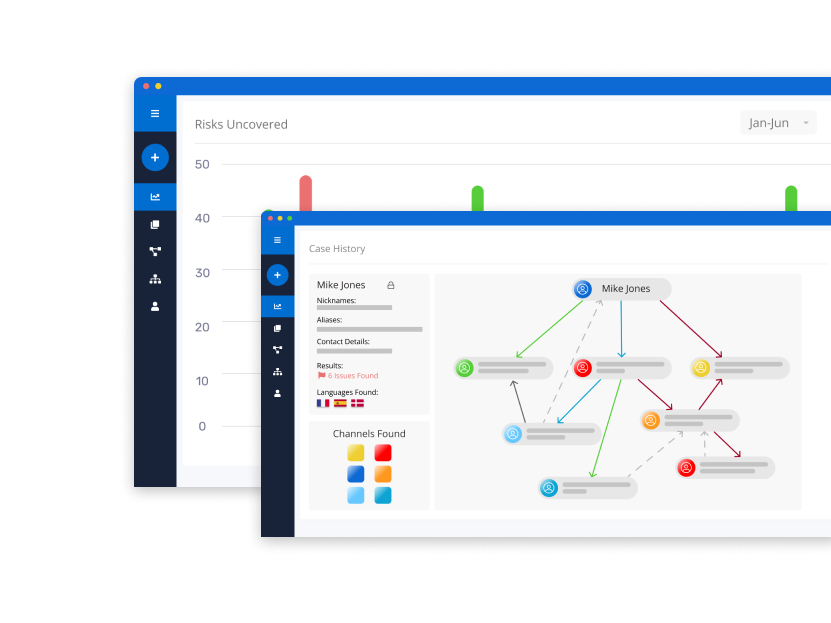
Experience Lightning-Fast and Intelligent Investigations with Our Advanced Open Source Intelligence Tool
Intelligent and Investigative
Smarter decision-making by automating data filtering and analysis from internal and external sources to highlight vital information.
Analysis & Visualisation
Discover links and network mapping using interactive charts, detailed data view and reporting efficiency. Deep-dive into the data to derive valuable insights.
Speed and Accuracy
Work faster and eliminate errors by accessing all data sources from Neotas Enhanced Due Diligence platform in a single dashboard.
Secure & Transparent
Maintain privacy and anonymity while conducting due diligence. Complete control on your investigations and data utilisation.
What is OSINT and Why is it important?
Open Source Intelligence (OSINT) is the application of intelligence gathering techniques and technology to investigations that make use of open source data (OSD).
To ensure that the evidence is secure, investigators need to keep track of all of their OSINT sources, including screenshots and timestamps of important findings, and log all of their activities so that it’s possible to check that an investigation was carried out thoroughly. It is also important to check facts, avoid pretexting, and check for bias when conducting OSINT investigations. And this is where Neotas Enhanced Due Diligence Platform can help!
Enhanced decision-making
OSINT provides insights into security threats, market trends, competitor analysis, and consumer behavior. By leveraging OSINT, organisations can make informed decisions based on up-to-date and relevant information.
Improved security and risk management
OSINT allows companies to gather data on potential threats and implement appropriate security measures to mitigate business risks effectively.
Cost-effective data gathering
OSINT leverages publicly available information that is often free, eliminating the need for financial investment in data acquisition.
Eliminate Process Inefficiencies
The Neotas Due Diligence platform offers a user-friendly and efficient solution for due diligence research by centralising source links, providing QA visibility, automating report template selection and content population, streamlining multi-source querying, and simplifying source access with automated means. These features collectively contribute to a more effective and productive due diligence process.
- Centralise and organise all source links from different jurisdictions, making it easier for researchers to access and explore relevant information.
- Quality Assurance (QA) teams can track and review the complete history of queries run by researchers during the due diligence process.
- Simplifies the reporting process by automatically presenting the most up-to-date report templates tailored to specific clients and use cases.
- Automatically pre-populates relevant findings and identifiers into a predefined report template.
- Simplifies the data retrieval process by allowing researchers to send queries to multiple sources simultaneously using a single input.
- Automated source querying to eliminate username/password hassles, simplifying the research workflow and enhancing security.
Quality Improvements and Save Cost
Revolutionise due diligence with our cutting-edge platform! Automated internet searches, multilingual capabilities, and dynamic research checklists streamline the process. Discover connections across sources with network analysis, and upskill analysts with automatic OSINT techniques. Stay ahead with efficiency, accuracy, and unrivaled insights!
- Automated internet searches for consistent and quality results with pre-defined parameters, such as Boolean queries using identifier variations, to ensure consistency and gather high-quality results.
- Multilingual capabilities for comprehensive search allowing researchers to access information as a native speaker would, ensuring comprehensive and accurate results from sources in different linguistic contexts.
- Dynamic research methodology checklist for structured analysis and comments. Analysts and QAs can enter comments and notes at each step, promoting collaboration and ensuring a well-documented research process.
- Network analysis to connect data from various sources for a holistic view, revealing potential associations and risks that might otherwise be missed in disjointed databases.
- Automatic OSINT techniques to upskill analysts’ digital footprint discovery. This includes uncovering online information, social media presence, digital records, and other relevant data that contribute to a more comprehensive understanding of the subjects under investigation.
Unleash the Power of OSINT for Actionable Business Intelligence
We leverage Open source intelligence (OSINT) to use publicly available data to provide organisations with hyper-accurate and fully auditable insights with no false positives.
Improve Efficiencies
Improve analyst efficiencies, including cost and time reduction of minimum 25% with zero false positives.
Reduce Blindspots
The FCA recommends open source Internet checks as best practice (FG 18/5). Manage and reduce risk by incorporating 100% of online sources into your processes.
Ongoing Monitoring
Manage risk with hyper accurate ongoing monitoring. We will monitor 100% of publicly available online data to help identify relevant risks.
Book A Demo
Resources on OSINT
Our clients can choose to use our advanced technology to interrogate vast data sources using their own methodologies. Our team of in-house expert analysts can also produce reports for you.
Trusted By Global Organisations
Neotas Open Source Intelligence Software can take your open source intelligence investigations to the next level














Frequently Asked Questions on OSINT
OSINT stands for Open-Source Intelligence and refers to the collection and analysis of publicly available information from various sources such as social media, news articles, websites, and public records.
OSINT provides organizations with access to publicly available information, allowing them to gather intelligence, identify potential threats, and make informed decisions. It is also crucial for cybersecurity, as it helps in detecting and mitigating risks.
The OSINT process involves several steps. It begins with defining the objectives and the information needed. Then, data is collected from open sources using various tools and techniques. The collected information is then processed, analyzed, and validated to extract meaningful insights. Finally, the findings are disseminated to the relevant stakeholders.
There are numerous tools and techniques available for OSINT. These include search engines, social media monitoring tools, data mining and analysis software, web scraping tools, and specialized platforms designed for OSINT purposes. Techniques such as keyword searching, data visualization, and link analysis are commonly used to extract valuable information from large datasets.
While OSINT is a valuable tool for intelligence gathering, it has some limitations. These include limited access to classified information, potential for misinformation, an overwhelming amount of data, lack of context, and the inability to verify information. It’s essential to use OSINT alongside other sources to ensure accurate and informed decision-making.
OSINT and open-source data (OSD) may be used interchangeably, but they are distinct concepts. OSD refers to publicly available information sourced from the internet, including social media, online news, and sanctions lists. On the other hand, OSINT is the outcome of studying, analyzing, and using OSD to make informed decisions. While anyone can access and gather OSD, it takes trained investigators to turn that information into valuable OSINT insights.
OSINT investigations refer to the process of gathering and analysing publicly available information to gather insights, uncover connections, and support investigative efforts.
Financial services utilize OSINT for AFC and AML efforts to combat financial crime and money laundering effectively.
Corporations rely on OSINT to protect their brand from financial and reputational risks, resolve identities of fraudsters, and perform enhanced due diligence on stakeholders.
Government and law enforcement agencies leverage OSINT to understand networks involved in serious crime, disrupt international border crime, and counter terrorism.
Risk consultancies benefit from OSINT, enabling analysts and investigators to conduct swift and thorough investigations for multiple clients.
OSINT technology empowers various sectors, including law enforcement, finance, cybersecurity, and business intelligence, by providing valuable insights, enabling proactive decision-making, and mitigating potential risks.
Comprehensive Intelligence Gathering: OSINT allows you to collect vast amounts of publicly available information from diverse online sources, providing a comprehensive view of your subject of interest.
Enhanced Due Diligence: By leveraging OSINT, you can conduct in-depth background checks on individuals, companies, or entities, enabling better risk assessment and informed decision-making.
Investigative Insights: OSINT technology helps investigators uncover crucial insights and connections, aiding in solving cases, identifying potential risks, and uncovering hidden patterns.
Reputation Management: OSINT assists in monitoring online reputation, brand mentions, and social media sentiment, helping businesses proactively manage their image and respond to potential crises.
Threat Detection and Prevention: OSINT enables the identification of potential security threats, cyberattacks, or emerging risks, allowing organizations to take proactive measures to prevent incidents.
Competitive Intelligence: Through OSINT, businesses can gather intelligence on competitors, market trends, and industry developments, enabling strategic decision-making and market positioning.
Fraud Prevention: OSINT aids in detecting fraudulent activities by analyzing online behavior, uncovering fake identities, and identifying suspicious patterns.
Situational Awareness: OSINT provides real-time and up-to-date information on events, disasters, or incidents, enhancing situational awareness for businesses and organizations.
Humanitarian Efforts: OSINT can support humanitarian organizations in crisis response by providing valuable data on affected regions, aiding relief efforts, and locating missing persons.
Cybersecurity Analysis: OSINT helps cybersecurity professionals gather threat intelligence, identify potential vulnerabilities, and assess the cybersecurity landscape.
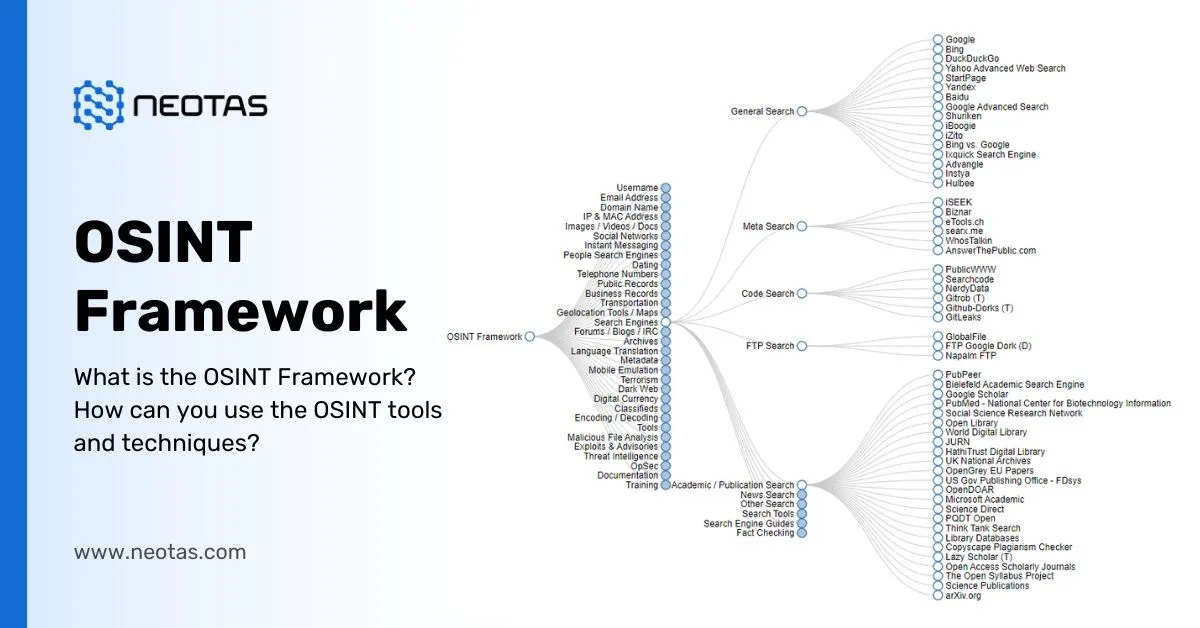
The OSINT framework refers to a structured approach that combines data, procedures, methodologies, and various tools to aid security teams in swiftly and accurately uncovering information about potential adversaries or their activities. By utilizing an OSINT framework, security professionals can effectively establish the digital footprint of a known threat.
The OSINT framework typically includes the following key steps:
Planning: Define the objectives of the OSINT operation, identify the target of interest, and outline the scope and resources needed for the investigation.
Collection: Gather relevant information from open sources such as social media platforms, websites, public records, news articles, and other publicly available data.
Processing: Organize and categorize the collected data for easier analysis. This step involves removing duplicates, verifying sources, and ensuring data integrity.
Analysis: Evaluate the information to extract meaningful insights, patterns, and connections. Analyze the data to identify potential risks, opportunities, or threats.
Collaboration: Share findings and collaborate with other stakeholders or team members to gain additional perspectives and insights.
Reporting: Prepare a comprehensive and structured report presenting the findings, analysis, and conclusions of the OSINT operation.
Validation: Validate the accuracy and reliability of the information obtained, ensuring that it aligns with the overall objectives of the investigation.
The OSINT framework is a valuable tool for various fields, including intelligence agencies, law enforcement, cybersecurity, corporate security, and business intelligence. It provides a structured and systematic approach to harness the vast amount of publicly available information on the internet, enabling organizations to make informed decisions, identify potential risks, and stay ahead of emerging threats.
OSINT tools operate entirely within the bounds of the law since they solely rely on information accessible through “open sources.” These sources do not encompass any proprietary or confidential data stored within an organization’s databases; instead, they are limited to publicly available information.
open source intelligence tools
open source intelligence techniques
open source intelligence framework
OSINT investigation tools
OSINT for cybersecurity
open source intelligence software
OSINT training programs
advanced OSINT techniques
OSINT for threat intelligence
OSINT automation tools
OSINT data collection methods
real-time OSINT solutions
OSINT for law enforcement
OSINT for business intelligence
cloud-based OSINT platforms
OSINT for penetration testing
OSINT social media analysis
open source threat intelligence tools
OSINT for competitive analysis
AI-powered OSINT tools
OSINT data scraping tools
open source intelligence gathering
OSINT in cyber investigations
OSINT for fraud detection
OSINT threat assessment
OSINT for risk management
geospatial OSINT tools
OSINT for digital forensics
automated OSINT solutions
OSINT APIs for developers
OSINT for compliance monitoring
OSINT for public sector intelligence
OSINT for financial crime investigations
OSINT techniques for beginners
OSINT in crisis response
OSINT in counter-terrorism
OSINT for national security
OSINT in corporate investigations
OSINT for brand protection
open source cyber threat intelligence
OSINT case studies
OSINT advanced methodologies
OSINT for fake news detection
OSINT for social engineering prevention
OSINT in intelligence operations
OSINT techniques for deep web research
free OSINT tools
OSINT for enterprise security
OSINT and data privacy
OSINT in the legal industry
OSINT in academic research
OSINT tutorials and resources
OSINT and ethical hacking
OSINT for disaster response
OSINT data visualization tools
OSINT intelligence reports
OSINT for reputation management
OSINT for social media monitoring
OSINT software for journalists
OSINT for government intelligence
OSINT and machine learning integration
OSINT for malware analysis
OSINT cloud services
OSINT network monitoring tools
OSINT in counterintelligence
OSINT platforms for law enforcement
OSINT in emergency response
OSINT case management tools
OSINT advanced search engines
OSINT browser extensions
OSINT for environmental intelligence
OSINT in humanitarian aid
OSINT for supply chain security
OSINT in privacy investigations
OSINT data mining techniques
OSINT for open data analysis
OSINT for NGO operations
OSINT tools for market research
OSINT in global intelligence
OSINT for policy-making
OSINT for human rights monitoring
OSINT intelligence lifecycle
OSINT for situational awareness
OSINT for web application testing
OSINT dashboards and analytics
OSINT and blockchain analysis
OSINT forensic tools
OSINT reconnaissance tools
OSINT for IoT security
OSINT and cyber threat hunting
OSINT and threat actor profiling
OSINT for identity verification
OSINT and intellectual property protection
OSINT in digital risk management
OSINT incident response tools
OSINT for phishing prevention
OSINT and dark web monitoring
OSINT and database scraping
OSINT for information security awareness
OSINT web crawling frameworks
OSINT for law firm investigations
OSINT for personal data protection
OSINT and information warfare
OSINT in journalism investigations
OSINT for data breach investigations
OSINT software for open-source ecosystems
OSINT best practices for security teams
OSINT for tracking illicit activities
OSINT for human resource investigations
OSINT for investment research
OSINT integration with SIEM systems
OSINT ethical considerations
OSINT for vulnerability assessment
OSINT and geopolitical analysis
OSINT and misinformation campaigns
OSINT for predictive analytics
advanced OSINT tools for investigations
comprehensive OSINT frameworks for analysis
cutting-edge OSINT techniques for security
best open source intelligence tools for research
top OSINT investigation tools for professionals
effective OSINT techniques for data collection
innovative open source intelligence tools
complete open source intelligence frameworks
advanced OSINT investigation software solutions
OSINT tools for cybersecurity and threat analysis
modern open source intelligence investigation methods
real-time OSINT tools for threat monitoring
all-in-one OSINT frameworks for intelligence gathering
expert OSINT investigation tools for professionals
AI-powered open source intelligence tools
OSINT techniques for social media investigations
best practices for using OSINT tools
open source intelligence methods for businesses
OSINT tools for corporate intelligence analysis
cloud-based OSINT frameworks for research
customizable open source intelligence techniques
dynamic OSINT platforms for investigators
real-time OSINT analysis tools for enterprises
OSINT strategies for efficient investigations
user-friendly open source intelligence frameworks
cloud-integrated OSINT tools for security teams
high-performance open source intelligence systems
OSINT frameworks for digital forensics
specialized OSINT techniques for investigators
top-rated open source intelligence platforms
scalable OSINT investigation software solutions
data-driven open source intelligence tools
real-time open source intelligence software
enterprise-ready OSINT frameworks for intelligence
OSINT platforms for advanced threat detection
open source intelligence solutions for analysts
custom OSINT tools for investigative workflows
next-gen OSINT investigation tools
flexible open source intelligence techniques
highly adaptive OSINT platforms for research
end-to-end OSINT frameworks for analysts
modern open source intelligence tools for beginners
OSINT platforms for advanced social media monitoring
effective OSINT techniques for crime investigations
user-friendly OSINT investigation platforms
real-time open source intelligence analysis solutions
OSINT frameworks for enterprise intelligence gathering
specialized OSINT investigation tools for professionals
all-purpose open source intelligence platforms
strategic OSINT techniques for investigative success
open source intelligence solutions for data analysts
comprehensive OSINT techniques for security professionals
integrated open source intelligence software platforms
modern OSINT tools for threat intelligence operations
cloud-based open source intelligence tools for research
advanced open source intelligence investigation methods
OSINT frameworks designed for security experts
professional-grade OSINT tools for investigators
innovative open source intelligence systems
OSINT solutions for business intelligence operations
versatile open source intelligence platforms
cloud-hosted OSINT investigation tools
data-centric OSINT frameworks for research
real-time open source intelligence monitoring tools
high-performance OSINT platforms for analysis
customizable open source intelligence systems
next-generation OSINT techniques for security experts
intelligent OSINT tools for efficient investigations
scalable open source intelligence platforms for enterprises
highly effective OSINT frameworks for businesses
cloud-optimized open source intelligence investigation tools
advanced OSINT analysis techniques for investigators
cutting-edge open source intelligence investigation solutions
OSINT tools optimized for modern threat analysis
real-time OSINT monitoring and investigation systems
OSINT techniques for enhanced data gathering
AI-driven open source intelligence investigation platforms
top-rated open source intelligence software tools
modern OSINT solutions for corporate investigations
cloud-integrated OSINT systems for professionals
OSINT investigation platforms for security specialists
scalable open source intelligence techniques for research
custom OSINT investigation tools for security analysts
user-focused OSINT frameworks for intelligence gathering
open source intelligence solutions for enterprises
OSINT platforms designed for investigative professionals
AI-enhanced open source intelligence systems
integrated OSINT analysis tools for security experts
cloud-ready OSINT frameworks for research
innovative open source intelligence tools for analysts
specialized OSINT techniques for digital investigations
comprehensive open source intelligence software platforms
real-time OSINT platforms for investigative workflows
advanced open source intelligence solutions for analysts
effective OSINT techniques for corporate investigations
next-gen open source intelligence platforms for professionals
customizable OSINT investigation frameworks
open source intelligence solutions for cybersecurity operations
dynamic OSINT systems for efficient investigations
cloud-powered OSINT platforms for intelligence gathering
data-focused OSINT investigation tools for research
real-time open source intelligence tools for professionals
enterprise-level OSINT frameworks for security analysis
advanced OSINT tools for social media monitoring
AI-powered OSINT solutions for investigators
tailored open source intelligence techniques for enterprises
cloud-ready OSINT tools for security workflows
OSINT platforms for real-time intelligence operations
cutting-edge OSINT frameworks for advanced investigations
modern open source intelligence solutions for analysts
open source intelligence New York
open source intelligence Los Angeles
open source intelligence Chicago
open source intelligence Houston
open source intelligence Miami
open source intelligence San Francisco
open source intelligence Dallas
open source intelligence Washington DC
open source intelligence Boston
open source intelligence Seattle
open source intelligence Philadelphia
open source intelligence Denver
open source intelligence Atlanta
open source intelligence Detroit
open source intelligence Minneapolis
open source intelligence Austin
open source intelligence Charlotte
open source intelligence Tampa
open source intelligence Orlando
open source intelligence Phoenix
open source intelligence London
open source intelligence Manchester
open source intelligence Birmingham
open source intelligence Leeds
open source intelligence Glasgow
open source intelligence Edinburgh
open source intelligence Liverpool
open source intelligence Belfast
open source intelligence Dublin
open source intelligence Cardiff
open source intelligence Bristol
open source intelligence Nottingham
open source intelligence Sheffield
open source intelligence Leicester
open source intelligence Southampton
open source intelligence Paris
open source intelligence Lyon
open source intelligence Marseille
open source intelligence Toulouse
open source intelligence Bordeaux
open source intelligence Nice
open source intelligence Berlin
open source intelligence Munich
open source intelligence Frankfurt
open source intelligence Hamburg
open source intelligence Cologne
open source intelligence Stuttgart
open source intelligence Dusseldorf
open source intelligence Vienna
open source intelligence Amsterdam
open source intelligence Brussels
open source intelligence Zurich
open source intelligence Geneva
open source intelligence Milan
open source intelligence Rome
open source intelligence Madrid
open source intelligence Barcelona
open source intelligence Valencia
open source intelligence Lisbon
open source intelligence Prague
open source intelligence Warsaw
open source intelligence Budapest
open source intelligence Stockholm
open source intelligence Oslo
open source intelligence Copenhagen
open source intelligence Helsinki
open source intelligence Luxembourg City
open source intelligence Tallinn
open source intelligence Riga
open source intelligence Vilnius
osint tools New York
osint tools Los Angeles
osint tools Chicago
osint tools Houston
osint tools Miami
osint tools San Francisco
osint tools Dallas
osint tools Washington DC
osint tools Boston
osint tools Seattle
osint tools Philadelphia
osint tools Denver
osint tools Atlanta
osint tools Detroit
osint tools Minneapolis
osint tools Austin
osint tools Charlotte
osint tools Tampa
osint tools Orlando
osint tools Phoenix
osint tools London
osint tools Manchester
osint tools Birmingham
osint tools Leeds
osint tools Glasgow
osint tools Edinburgh
osint tools Liverpool
osint tools Belfast
osint tools Dublin
osint tools Cardiff
osint tools Bristol
osint tools Nottingham
osint tools Sheffield
osint tools Leicester
osint tools Southampton
osint tools Paris
osint tools Lyon
osint tools Marseille
osint tools Toulouse
osint tools Bordeaux
osint tools Nice
osint tools Berlin
osint tools Munich
osint tools Frankfurt
osint tools Hamburg
osint tools Cologne
osint tools Stuttgart
osint tools Dusseldorf
osint tools Vienna
osint tools Amsterdam
osint tools Brussels
osint tools Zurich
osint tools Geneva
osint tools Milan
osint tools Rome
osint tools Madrid
osint tools Barcelona
osint tools Valencia
osint tools Lisbon
osint tools Prague
osint tools Warsaw
osint tools Budapest
osint tools Stockholm
osint tools Oslo
osint tools Copenhagen
osint tools Helsinki
osint tools Luxembourg City
osint tools Tallinn
osint tools Riga
osint tools Vilnius
osint framework New York
osint framework Los Angeles
osint framework Chicago
osint framework Houston
osint framework Miami
osint framework San Francisco
osint framework Dallas
osint framework Washington DC
osint framework Boston
osint framework Seattle
osint framework Philadelphia
osint framework Denver
osint framework Atlanta
osint framework Detroit
osint framework Minneapolis
osint framework Austin
osint framework Charlotte
osint framework Tampa
osint framework Orlando
osint framework Phoenix
osint framework London
osint framework Manchester
osint framework Birmingham
osint framework Leeds
osint framework Glasgow
osint framework Edinburgh
osint framework Liverpool
osint framework Belfast
osint framework Dublin
osint framework Cardiff
osint framework Bristol
osint framework Nottingham
osint framework Sheffield
osint framework Leicester
osint framework Southampton
osint framework Paris
osint framework Lyon
osint framework Marseille
osint framework Toulouse
osint framework Bordeaux
osint framework Nice
osint framework Berlin
osint framework Munich
osint framework Frankfurt
osint framework Hamburg
osint framework Cologne
osint framework Stuttgart
osint framework Dusseldorf
osint framework Vienna
osint framework Amsterdam
osint framework Brussels
osint framework Zurich
osint framework Geneva
osint framework Milan
osint framework Rome
osint framework Madrid
osint framework Barcelona
osint framework Valencia
osint framework Lisbon
osint framework Prague
osint framework Warsaw
osint framework Budapest
osint framework Stockholm
osint framework Oslo
osint framework Copenhagen
osint framework Helsinki
osint framework Luxembourg City
osint framework Tallinn
osint framework Riga
osint framework Vilnius
osint techniques New York
osint techniques Los Angeles
osint techniques Chicago
osint techniques Houston
osint techniques Miami
osint techniques San Francisco
osint techniques Dallas
osint techniques Washington DC
osint techniques Boston
osint techniques Seattle
osint techniques Philadelphia
osint techniques Denver
osint techniques Atlanta
osint techniques Detroit
osint techniques Minneapolis
osint techniques Austin
osint techniques Charlotte
osint techniques Tampa
osint techniques Orlando
osint techniques Phoenix
osint techniques London
osint techniques Manchester
osint techniques Birmingham
osint techniques Leeds
osint techniques Glasgow
osint techniques Edinburgh
osint techniques Liverpool
osint techniques Belfast
osint techniques Dublin
osint techniques Cardiff
osint techniques Bristol
osint techniques Nottingham
osint techniques Sheffield
osint techniques Leicester
osint techniques Southampton
osint techniques Paris
osint techniques Lyon
osint techniques Marseille
osint techniques Toulouse
osint techniques Bordeaux
osint techniques Nice
osint techniques Berlin
osint techniques Munich
osint techniques Frankfurt
osint techniques Hamburg
osint techniques Cologne
osint techniques Stuttgart
osint techniques Dusseldorf
osint techniques Vienna
osint techniques Amsterdam
osint techniques Brussels
osint techniques Zurich
osint techniques Geneva
osint techniques Milan
osint techniques Rome
osint techniques Madrid
osint techniques Barcelona
osint techniques Valencia
osint techniques Lisbon
osint techniques Prague
osint techniques Warsaw
osint techniques Budapest
osint techniques Stockholm
osint techniques Oslo
osint techniques Copenhagen
osint techniques Helsinki
osint techniques Luxembourg City
osint techniques Tallinn
osint techniques Riga
osint techniques Vilnius