TPRM Questionnaire
In Third-Party Risk Management (TPRM), a comprehensive and well-designed questionnaire serves as a critical tool for assessing the risk posture of third-party entities. These questionnaires are designed to gather pertinent information about a vendor’s security practices, operational resilience, compliance adherence, and overall risk management capabilities. By leveraging a robust TPRM questionnaire, organisations can gain valuable insights that inform their decision-making processes and guide the development of effective risk mitigation strategies.
The creation of an effective TPRM questionnaire requires a meticulous approach that considers the unique requirements of the organisation, the specific third-party relationship, and the applicable regulatory and industry standards. A well-crafted questionnaire should strike a balance between comprehensiveness and practicality, ensuring that it captures essential information without imposing an undue burden on the third party.
A TPRM Questionnaire serves as a structured tool to evaluate vendors’ risk profiles and compliance status. This document provides a comprehensive questionnaire covering all critical aspects of vendor risk assessment.
When developing a TPRM questionnaire, it is advisable to follow a structured approach that covers various aspects of third-party risk management.
TPRM questionnaire:
1. General Company Information
Understanding the vendor’s background and operational structure is fundamental to assessing their risk level.
Company Details:
- Legal name of the company:
- Trade name (if applicable):
- Business registration number:
- Country of incorporation:
- Headquarters address:
- Other operational locations:
- Website:
Company Structure & Leadership:
- Type of entity (e.g., Corporation, LLC, Partnership):
- Parent company (if applicable):
- Subsidiaries or affiliates:
- Key executives and leadership team:
- Contact information for risk, security, and compliance teams:
Business Operations & Market Position:
- Number of employees:
- Years in operation:
- Primary industry and market segment:
- Summary of core services or products provided:
- Key customers or sectors served:
- Revenue range (optional):
2. Information Security & Data Protection
Data security is a primary concern when engaging third-party vendors, particularly those handling sensitive or customer data.
Information Security Policies & Standards:
- Do you have a formal Information Security Policy?
- Are you certified or compliant with industry standards (ISO 27001, NIST, SOC 2, etc.)?
- Do you enforce security controls for data access, transmission, and storage?
- How do you monitor and respond to security threats?
- Have you conducted a security risk assessment in the last 12 months?
Data Protection & Privacy:
- What measures do you implement for data encryption (in transit and at rest)?
- Do you conduct regular vulnerability assessments and penetration testing?
- What authentication and access control mechanisms are in place?
- How do you handle personally identifiable information (PII) or sensitive customer data?
- Do you have a Data Loss Prevention (DLP) strategy?
- Have you experienced any security breaches in the last two years, and if so, how were they managed?
3. Compliance & Regulatory Requirements
Vendors must align with applicable laws and industry regulations to mitigate legal and financial risks.
Regulatory Compliance:
- What legal and regulatory frameworks do you comply with? (e.g., GDPR, HIPAA, PCI-DSS, CCPA)
- Have you undergone external security audits?
- Can you provide compliance certifications and reports?
- Do you have a Data Processing Agreement (DPA) with your clients?
Audit & Reporting:
- Do you conduct periodic internal security audits?
- How do you handle non-compliance or policy violations?
- How do you report compliance violations or breaches?
4. Business Continuity & Disaster Recovery
Assessing the vendor’s ability to operate during disruptions is essential for business resilience.
Continuity & Recovery Plans:
- Do you have a documented Business Continuity Plan (BCP)?
- How frequently do you test your Disaster Recovery Plan (DRP)?
- What are your Recovery Time Objective (RTO) and Recovery Point Objective (RPO)?
- How do you ensure operational resilience in case of cybersecurity incidents?
Crisis Management:
- Have you experienced major service outages in the last two years?
- How do you communicate disruptions to your customers?
- Do you have an alternative data centre or backup location?
5. Vendor Risk Management & Subcontractors
Understanding a vendor’s dependency on subcontractors helps assess risk at multiple levels.
- Do you rely on subcontractors for service delivery?
- How do you evaluate and monitor third-party subcontractors?
- Can you provide a list of subcontractors with access to sensitive data?
- How do you ensure subcontractors comply with security policies?
- Do you conduct periodic audits of your subcontractors to ensure compliance?
6. Incident Response & Reporting
A vendor’s incident response capability is critical to mitigating damage from security breaches.
- Do you have a formal Incident Response Plan?
- What is your process for reporting security incidents and data breaches?
- Have you experienced any significant security breaches in the past 12 months?
- How do you notify affected parties in case of an incident?
- Do you conduct incident response simulations?
- Do you have a well-defined communication plan in place to inform stakeholders during an incident?
7. Financial Stability & Insurance
A vendor’s financial health impacts its ability to deliver services consistently.
- Can you provide financial statements for the last two years?
- What measures do you have in place to ensure financial stability?
- Do you have cyber liability insurance?
- What is your policy for compensating customers in case of service disruptions?
8. Physical & Infrastructure Security
Physical security measures are crucial to preventing unauthorised access to sensitive systems.
- How do you secure your physical office locations and data centres?
- Do you have access control mechanisms in place?
- Is your infrastructure monitored 24/7?
- How do you handle employee and visitor access?
9. Human Resources & Employee Training
Employee awareness and training are vital components of risk mitigation.
- Do you conduct background checks for employees handling sensitive data?
- How often do employees receive cybersecurity training?
- What are your policies for managing insider threats?
- Do you have remote work security guidelines?
10. Contractual Agreements & Legal Considerations
Contracts should define expectations, liabilities, and security obligations.
- Can you provide copies of your standard Service Level Agreements (SLAs)?
- What are your data protection obligations under contracts?
- How do you handle contract termination and data destruction?
- Do you have legal dispute resolution mechanisms?
TPRM Questionnaire Example
Here is a sample set of questions that could be included in a comprehensive Third-Party Risk Management (TPRM) questionnaire:
Organisational Overview:
1. Provide an overview of your organisation, including legal name, locations, years of operation, and primary business activities.
2. Describe your organisational structure, ownership, and governance practices.
3. Have there been any recent mergers, acquisitions, or significant changes that may impact your risk profile?
Information Security and Cybersecurity:
4. Do you have documented information security policies, standards, and procedures in place?
5. Describe your access control and identity management practices, including mechanisms for user provisioning, authentication, and authorisation.
6. What data protection and encryption measures do you have in place for data at rest and in transit?
7. Provide details about your network security architecture, including firewalls, intrusion detection/prevention systems, and segmentation strategies.
8. Describe your vulnerability management and patch management processes.
9. Do you have an incident response plan and breach notification protocols in place?
10. What security awareness training and employee background check processes do you have in place?
Data Privacy and Compliance:
11. Describe how you ensure compliance with relevant data privacy regulations (e.g., GDPR, HIPAA, PCI DSS).
12. What are your data handling practices and data retention policies?
13. How do you protect sensitive or confidential information, including personal data and intellectual property?
Business Continuity and Disaster Recovery:
14. Do you have documented business continuity and disaster recovery plans in place?
15. Describe your backup and recovery strategies for data and systems.
16. What redundant infrastructure or failover mechanisms do you have in place?
17. How often do you test and validate your recovery procedures?
Vendor Management and Supply Chain:
18. Do you rely on any sub-contractors or additional vendors within your supply chain?
19. If so, describe your vendor management practices, including due diligence and monitoring processes.
Financial Stability and Insurance:
20. Provide your most recent financial statements or credit rating information.
21. Do you have relevant insurance policies in place (e.g., cyber insurance, professional liability insurance)?
Physical Security and Environmental Controls:
22. Describe the physical security measures and access controls in place at your facilities.
23. What environmental controls and measures do you have to protect against threats or natural disasters?
Human Resources and Personnel Management:
24. Describe your processes for conducting background checks and employee screening.
25. Do you have security awareness training programs and non-disclosure agreements in place for employees?
26. What processes do you have for managing employee terminations or role changes?
Audit and Compliance:
27. Describe your internal audit processes and frequency.
28. Have you undergone any external audits or obtained relevant certifications (e.g., ISO 27001, SOC 2)?
29. How do you address and remediate identified issues or non-conformities?
Additional Requirements (Customise as needed):
30. Provide any additional information or documentation relevant to your specific industry or regulatory environment.
Please note that this is a sample set of questions, and the actual questionnaire should be tailored to the specific needs and requirements of your organisation and the third-party relationship being assessed. Additionally, the questionnaire should be complemented by other assessment techniques, such as on-site audits, security assessments, and documentation reviews, to gain a comprehensive understanding of the third party’s risk posture.
Download the TPRM Questionnaire Template
It is important to note that the TPRM questionnaire should be tailored to the specific nature of the third-party relationship and the associated risk factors. For low-risk relationships, a streamlined version of the questionnaire may suffice, while high-risk or critical relationships may necessitate a more comprehensive and in-depth assessment.
Furthermore, the questionnaire should be complemented by additional assessment techniques, such as on-site audits, security assessments, or the review of supporting documentation and evidence. A holistic approach that combines multiple assessment methods can provide a more accurate and comprehensive understanding of the third party’s risk posture.
Effective administration and follow-up processes are also crucial for maximising the value derived from the TPRM questionnaire. This may involve establishing clear timelines for response, conducting follow-up interviews or clarification sessions, and maintaining a centralised repository for storing and analysing the collected information.
Read more about Third-Party Risk, TPRM software, and TPRM processes.
Read the detailed guide on Vendor Due Diligence Checklist
TPRM Questionnaire
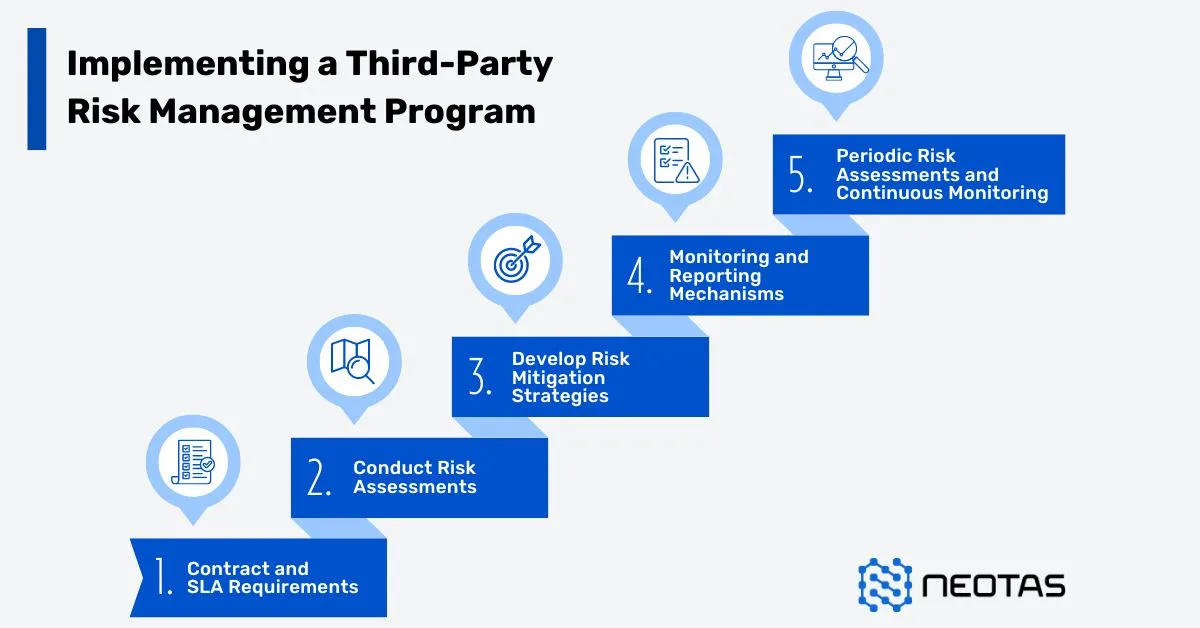
Implementation Roadmap
A well-structured Third-Party Risk Management (TPRM) questionnaire is essential for mitigating vendor risks, ensuring compliance, and maintaining operational resilience. However, simply having a questionnaire is not enough—it must be effectively embedded into the broader vendor risk management lifecycle.
By following a structured approach, organisations can proactively assess, monitor, and mitigate third-party risks while strengthening security, regulatory compliance, and business continuity.
To successfully integrate a TPRM questionnaire into your organisation’s risk management framework, follow this step-by-step roadmap:
Phase 1: Planning & Preparation
- Identify key stakeholders, including security, legal, compliance, procurement, and IT teams, to ensure a well-rounded risk assessment approach.
- Define risk assessment criteria based on vendor services, data access levels, regulatory obligations, and business impact.
- Develop or tailor the TPRM questionnaire to align with industry-specific risks, compliance requirements, and internal security policies.
Phase 2: Vendor Onboarding & Assessment
- Provide vendors with the questionnaire alongside clear instructions on completion, expected response formats, and submission deadlines.
- Implement an automated or structured scoring system to streamline evaluations and ensure consistent assessments.
- Validate responses through independent audits, security certifications, and compliance reviews.
- Maintain an open channel for vendors to clarify responses or request guidance on security expectations.
Phase 3: Risk Evaluation & Decision-Making
- Analyse vendor responses to identify key risk areas, such as data security weaknesses, non-compliance, or operational vulnerabilities.
- Categorise vendors into risk tiers (low, medium, high risk) to prioritise assessments based on potential business impact.
- Collaborate with vendors to develop remediation plans, setting clear corrective actions and deadlines for addressing identified risks.
Phase 4: Contractual & Compliance Alignment
- Ensure risk mitigation requirements, security obligations, and regulatory compliance are formally documented in vendor contracts.
- Define Service Level Agreements (SLAs) that cover data protection, incident response, business continuity, and performance expectations.
- Establish contractual clauses outlining penalties or termination rights for non-compliance with security obligations.
Phase 5: Ongoing Monitoring & Reassessment
- Conduct periodic reassessments (annually or biannually) to ensure vendors maintain compliance with evolving security and regulatory standards.
- Track vendor performance using Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs) to measure risk exposure effectively.
- Implement continuous monitoring processes, especially for vendors handling critical data, infrastructure, or sensitive operations.
- Engage internal audit teams or external assessors to validate vendor compliance and identify any emerging risks.
Phase 6: Incident Response & Continuous Improvement
- Establish a clear escalation process for security incidents involving third-party vendors, ensuring swift internal reporting and external notifications.
- Define communication protocols to ensure the right stakeholders are informed within set timeframes in the event of a breach.
- Continuously update the TPRM questionnaire to reflect emerging cyber threats, regulatory updates, and lessons from security incidents.
- Foster a culture of security awareness and collaboration with vendors, encouraging proactive risk mitigation and compliance efforts.
Best Practices for Implementing a TPRM Questionnaire
Effectively implementing a Third-Party Risk Management (TPRM) questionnaire requires a structured approach that ensures consistency, efficiency, and comprehensive risk assessment. Below are best practices to maximise the effectiveness of your TPRM process:
- Customise the Questionnaire Based on Vendor Type and Risk Level
Not all vendors pose the same level of risk. Customising the questionnaire based on vendor services, data access, and industry regulations ensures relevant information is collected. For high-risk vendors, additional security and compliance questions should be included.
- Utilise AI-Driven and Automated Tools
Leveraging AI-powered risk assessment platforms can enhance efficiency by automating questionnaire distribution, analysis, and scoring. These tools can flag inconsistencies, track changes over time, and provide real-time risk insights.
- Implement a Scoring System for Risk Prioritisation
Assign numerical scores to vendor responses to quantify risk exposure. A tiered scoring model (low, medium, high risk) can help prioritise follow-ups and deeper assessments for vendors that pose significant security or compliance concerns.
- Establish a Periodic Reassessment Strategy
Risk levels evolve over time, necessitating regular reassessments of third-party vendors. Establish a review cycle (e.g., annually or biannually) to ensure continued compliance and security alignment.
- Maintain a Centralised Vendor Risk Repository
A secure, centralised repository for vendor responses allows for easy tracking, trend analysis, and regulatory audits. This ensures quick access to historical data and risk mitigation plans if issues arise.
- Ensure Cross-Departmental Collaboration
TPRM should not be siloed within IT or procurement departments. Involving legal, compliance, finance, and operations teams ensures a holistic vendor risk management approach.
- Conduct Due Diligence Beyond the Questionnaire
Vendor responses should be validated through additional verification methods, including audits, penetration testing, financial assessments, and compliance checks. Blindly trusting self-reported answers can lead to significant risks.
- Monitor and Track Vendor Performance Over Time
Post-contract monitoring is essential to ensuring vendors adhere to security and compliance commitments. Establish Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs) to measure ongoing compliance and service quality.
- Require Vendors to Report Security Incidents Promptly
Incorporate contractual obligations that require vendors to notify your organisation of any security breaches, data leaks, or compliance violations. Define acceptable response times and remediation steps.
- Ensure Clear Communication of Expectations
From the outset, vendors should understand your organisation’s security, compliance, and operational expectations. Providing training or guidelines can help align third-party practices with internal risk management policies.
By integrating these best practices, organisations can strengthen their third-party risk management framework, ensuring vendors remain compliant, secure, and reliable.
Final Thoughts
Integrating a TPRM questionnaire into your risk management framework is not just about ticking compliance boxes—it’s about building a robust, proactive approach to vendor risk management. By prioritising due diligence, maintaining ongoing assessments, and ensuring strong contractual agreements, organisations can reduce risk exposure, strengthen regulatory compliance, and safeguard business continuity.
By following this structured roadmap, your organisation can stay ahead of evolving risks and build stronger, more resilient vendor relationships.
How can Neotas TPRM solutions help?
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM). In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Moreover, Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
If you’re curious about whether our third-party risk management solutions and services align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
Third Party Risk Management (TPRM) Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Vendor Due Diligence
- Open Source Intelligence (OSINT)
- Introducing the Neotas Enhanced Due Diligence Platform
Third Party Risk Management (TPRM) Case Studies:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation
- Risk-Based Approach (RBA) to AML & KYC risk management
- Anti-Money Laundering (AML)
- Supply Chain Risk Management
- Due Diligence Explained: Types, Checklist, Process, Reports



 Financial Crime Compliance Trends 2024
Financial Crime Compliance Trends 2024
























