TPRM meaning
TPRM stands for Third-Party Risk Management, and it refers to the comprehensive process of identifying, assessing, mitigating, and monitoring the potential risks associated with an organization’s engagement with third-party vendors, suppliers, or service providers. In today’s interconnected business landscape, where outsourcing and collaboration with external entities are commonplace, effective TPRM has become an essential component of an organization’s overall risk management strategy.
The primary objective of TPRM is to ensure that the risks posed by third-party relationships are appropriately managed, thereby safeguarding the organization’s reputation, financial stability, and compliance with relevant regulations and industry standards. It is a proactive approach that aims to protect an organization from the potential adverse consequences of third-party failures, data breaches, regulatory non-compliance, or other operational disruptions.
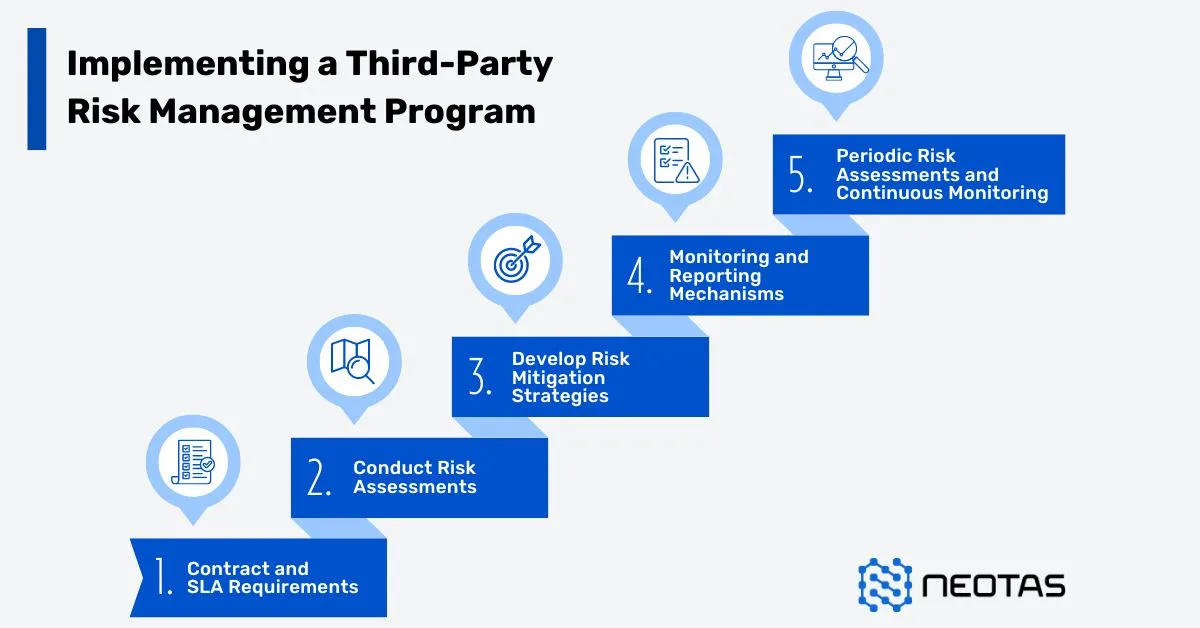
The TPRM process typically involves several key stages:
1. Third-Party Identification and Categorization:
The first step is to identify and categorize all third-party vendors, suppliers, or service providers with whom the organization has contractual relationships. This involves creating a comprehensive inventory and classifying these third parties based on the level of risk they pose to the organization, considering factors such as the nature of the services provided, access to sensitive data, and the criticality of the vendor to the organization’s operations.
2. Risk Assessment:
Once the third parties have been identified and categorized, a thorough risk assessment is conducted. This involves evaluating various risk factors, including financial stability, cybersecurity posture, data protection practices, business continuity plans, and compliance with relevant regulations and industry standards. The risk assessment may involve questionnaires, on-site audits, or third-party assessments conducted by independent organizations.
3. Risk Mitigation:
Based on the findings of the risk assessment, appropriate risk mitigation strategies are developed and implemented. These may include contractual provisions, security controls, monitoring mechanisms, or contingency plans. The goal is to reduce the potential impact of identified risks to an acceptable level while ensuring the continuity of business operations and the protection of sensitive information.
4. Ongoing Monitoring and Reporting:
TPRM is an ongoing process that requires continuous monitoring and reporting. This involves regularly reviewing third-party performance, conducting periodic reassessments, and ensuring that any changes in the third-party’s operations or risk profile are promptly identified and addressed. Regular reporting and communication with stakeholders, including senior management and relevant committees, are crucial to maintaining effective oversight and informed decision-making.
Effective TPRM requires a collaborative effort involving cross-functional teams from various departments within the organization, such as procurement, legal, information security, and risk management. It is essential to establish clear policies, procedures, and governance structures to ensure consistency and accountability throughout the TPRM lifecycle.
The benefits of implementing a robust TPRM program are multifaceted.
It helps organizations:
1. Mitigate operational, financial, and reputational risks associated with third-party relationships.
2. Enhance visibility and control over third-party activities and potential vulnerabilities.
3. Ensure compliance with relevant regulations, industry standards, and contractual obligations.
4. Build trust and confidence with stakeholders, including customers, partners, and regulatory bodies.
5. Improve decision-making processes by providing insights into third-party risk profiles.
6. Foster a culture of risk awareness and accountability across the organization.
In the ever-evolving business landscape, where third-party relationships are becoming increasingly complex and interconnected, TPRM has emerged as a crucial component of effective risk management. By adopting a comprehensive and proactive approach to TPRM, organizations can better navigate the risks associated with third-party engagements, protect their assets and reputation, and foster long-term sustainable business relationships.
Read more about Third-Party Risk, TPRM software, and TPRM processes.
Read the detailed guide on Vendor Due Diligence Checklist
TPRM meaning
How can Neotas TPRM solutions help?
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM). In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Moreover, Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
If you’re curious about whether our third-party risk management solutions and services align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
Third Party Risk Management (TPRM) Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Vendor Due Diligence
- Open Source Intelligence (OSINT)
- Introducing the Neotas Enhanced Due Diligence Platform
Third Party Risk Management (TPRM) Case Studies:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation
- Risk-Based Approach (RBA) to AML & KYC risk management
- Anti-Money Laundering (AML)
- Supply Chain Risk Management
- Due Diligence Explained: Types, Checklist, Process, Reports



 Financial Crime Compliance Trends 2024
Financial Crime Compliance Trends 2024
























