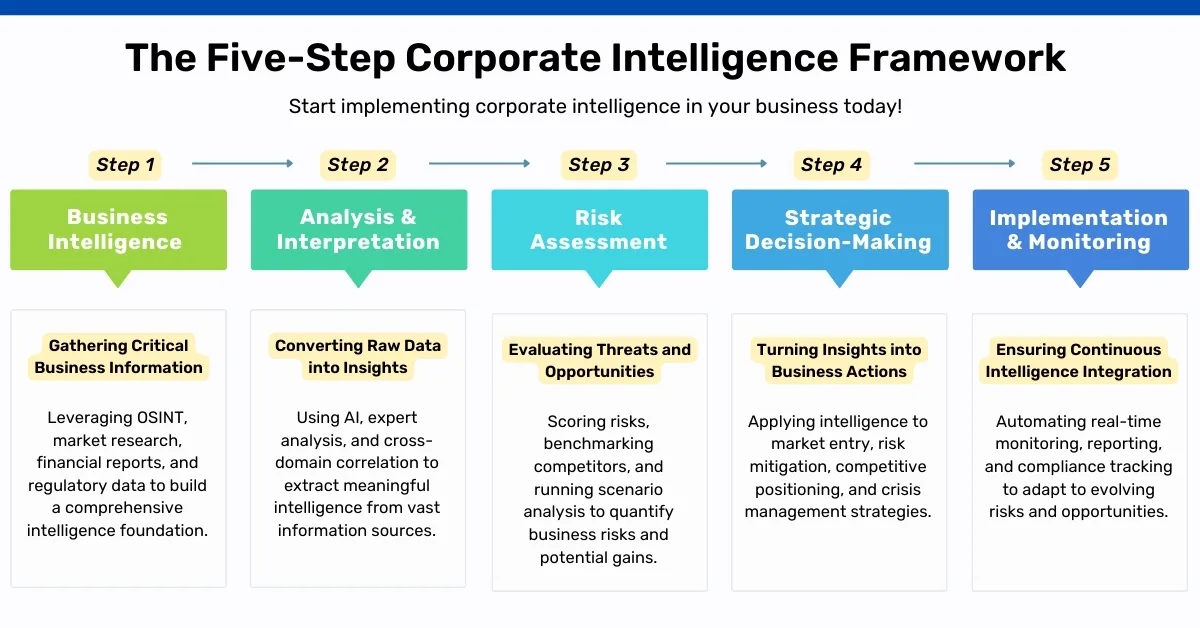
What is Risk Intelligence?
All you need to know about Strategic Risk Intelligence solutions, risk management framework and implementing a risk intelligence software to manage your business risk.
Risk intelligence, a concept that goes beyond traditional risk management, empowers organisations to navigate uncertainties with precision, agility, and foresight. It is a data-driven approach that integrates advanced analytics and strategic insights to ensure businesses remain resilient and competitive.
Modern businesses operate in environments influenced by globalisation, technological advancements, regulatory pressures, and evolving threats. Whether it’s managing financial risks, addressing cybersecurity vulnerabilities, or ensuring compliance, the need for a robust risk intelligence framework is more critical than ever. Risk intelligence enables organisations to not only mitigate risks but also leverage them as opportunities for growth.
Strategic Business Risk Intelligence
Risk intelligence is the systematic process of collecting, analysing, and applying data to identify, assess, and manage risks effectively. It combines advanced analytics, human expertise, and technological tools to provide actionable insights, enabling organisations to make informed decisions. Unlike traditional risk management, which often takes a reactive approach, risk intelligence is proactive, focusing on anticipating and mitigating risks before they materialise.
At its core, risk intelligence involves understanding the risk landscape, evaluating the likelihood and impact of various threats, and implementing strategies to address them. This approach empowers businesses to adapt to changes, seize opportunities, and safeguard their reputation and assets.
Importance of Risk Intelligence in Modern Businesses
The importance of risk intelligence lies in its ability to transform risk management from a defensive mechanism into a strategic enabler.
Key reasons why risk intelligence is essential for modern businesses include:
- Proactive Risk Mitigation: Risk intelligence equips organisations with the tools to identify emerging threats and act swiftly, minimising disruptions.
- Data-Driven Decision-Making: By leveraging analytics and real-time data, businesses can make more accurate and informed decisions.
- Enhanced Resilience: Organisations with robust risk intelligence frameworks can adapt to challenges, ensuring continuity in volatile environments.
- Regulatory Compliance: In industries with stringent regulations, risk intelligence ensures businesses remain compliant, avoiding fines and reputational damage.
- Competitive Advantage: Companies that manage risks effectively gain a competitive edge by maintaining stability and instilling confidence in stakeholders.
Risk intelligence is no longer a luxury but a necessity for organisations aiming to thrive in an unpredictable world.
The Evolution of Risk Management Practices to Risk Intelligence
Risk management has evolved significantly over the years. Traditionally, organisations adopted a reactive approach, addressing risks only after they occurred. However, the complexity of today’s risk landscape—driven by globalisation, digitisation, and interconnected economies—requires a more dynamic and forward-thinking approach.
From Reactive to Proactive
The shift from traditional risk management to risk intelligence represents a transition from reactive measures to proactive strategies. Risk intelligence leverages predictive analytics, machine learning, and big data to anticipate risks and minimise their impact. This evolution ensures businesses are not merely surviving risks but thriving despite them.
Technology as a Catalyst
The integration of technology, such as artificial intelligence (AI) and cloud-based platforms, has played a pivotal role in this transformation. These advancements enable organisations to analyse vast amounts of data, detect patterns, and forecast potential threats with greater accuracy and speed.
A Strategic Asset
Modern risk intelligence has transformed risk management into a strategic asset. It aligns closely with organisational goals, ensuring risks are managed in a way that supports growth, innovation, and sustainability.
The Fundamentals of Risk Intelligence
What Is Risk Intelligence?
Risk intelligence is an advanced form of risk management that focuses on using data and analytics to anticipate, assess, and address risks effectively. It goes beyond identifying threats, offering a comprehensive framework to understand risks in the context of an organisation’s objectives and environment.
Unlike traditional methods, risk intelligence is holistic, integrating diverse data sources—such as financial metrics, operational data, and external market trends—to provide a complete picture of an organisation’s risk profile. This approach enables businesses to adopt both defensive and offensive strategies, turning risks into opportunities.
Understanding Risk Intelligence as a Concept
At its heart, risk intelligence is about equipping decision-makers with the knowledge and tools to navigate uncertainty. It is based on three principles:
- Proactivity: Identifying risks before they occur.
- Data-Driven Insights: Leveraging data and analytics for accurate risk evaluation.
- Strategic Alignment: Ensuring risk management aligns with business goals.
Risk intelligence is not confined to a single department; it spans all areas of an organisation, from supply chain operations to financial planning and compliance. This integrated approach ensures that risks are managed cohesively, rather than in isolation.
Components of Risk Intelligence
Risk intelligence can be broken down into three key components:
- Assessment: The initial stage involves identifying and evaluating potential risks. This includes analysing historical data, market trends, and potential scenarios to determine the likelihood and impact of various threats.
- Monitoring: Continuous observation of internal and external environments is critical. Risk monitoring tools use real-time data to detect changes and provide alerts about emerging risks, ensuring organisations stay ahead of threats.
- Decision-Making: Risk intelligence supports informed decision-making by offering actionable insights. These insights enable organisations to implement mitigation strategies, allocate resources efficiently, and adjust operations as needed.
The Significance of Risk Quotient (RQ)
Risk Quotient (RQ) is a metric that quantifies an organisation’s ability to identify, assess, and respond to risks effectively. It reflects the maturity of an organisation’s risk intelligence capabilities, taking into account factors such as data utilisation, technology integration, and strategic alignment.
A high RQ indicates that an organisation is well-prepared to manage risks, adapt to challenges, and seize opportunities. Measuring and improving RQ is essential for businesses aiming to enhance their resilience and competitiveness.
Key Benefits of a High RQ:
- Enhanced Decision-Making: Data-driven insights lead to better strategic choices.
- Resilience: Organisations with high RQ can adapt to change and recover from disruptions.
- Stakeholder Confidence: Demonstrating a strong RQ builds trust among investors, partners, and customers.
By focusing on the fundamentals of risk intelligence and continuously improving their RQ, organisations can position themselves as leaders in their respective industries while safeguarding their future.
Key Elements of Risk Intelligence
Risk intelligence is built on a foundation of essential components that collectively help organisations navigate uncertainties with confidence. These elements—risk screening, due diligence, identity verification, account verification, and digital onboarding—play a vital role in creating a robust risk management framework. By addressing risks at multiple levels, businesses can not only mitigate threats but also foster trust and resilience in their operations.
Risk Screening
Risk screening is the first step in understanding potential threats to an organisation. It involves systematically identifying and assessing risks at their source, whether they arise from financial transactions, third-party relationships, or operational vulnerabilities.
- Methods and Tools for Risk Screening: Businesses use advanced tools, including AI-powered systems and real-time data analytics, to efficiently screen for risks. These tools enable companies to assess vast amounts of data, detect anomalies, and prioritise potential threats.
- Importance of Identifying Risks at the Source: Addressing risks early reduces their impact and prevents them from escalating into larger issues. For example, detecting fraudulent activities during the initial stages of a transaction can save both financial losses and reputational harm.
Risk screening acts as the first line of defence, equipping organisations with the knowledge needed to act decisively.
Due Diligence
Due diligence is the process of investigating and evaluating potential risks associated with specific entities, such as vendors, clients, or business partners. This critical step helps organisations make informed decisions and build trust.
- Steps in Conducting Due Diligence:
- Collect relevant information about the entity (e.g., background checks, financial records).
- Verify the accuracy of the data and cross-reference with trusted sources.
- Assess potential risks, such as legal or financial liabilities.
- Document findings and recommend appropriate actions.
- Examples of Due Diligence for Risk Mitigation: For instance, in financial transactions, due diligence can involve assessing a client’s creditworthiness and regulatory compliance. In supply chain management, it may include verifying a supplier’s adherence to ethical and legal standards.
Effective due diligence not only uncovers potential red flags but also enhances transparency and strengthens relationships with stakeholders.
Identity Verification
In an increasingly digital world, ensuring accurate identity verification is paramount for businesses. With the rise of online transactions and remote interactions, robust identity solutions are essential for reducing fraud and safeguarding operations.
- Ensuring Accurate Identity Verification: Modern identity verification relies on advanced technologies like biometric authentication, AI-based document analysis, and database cross-checking. These methods ensure that the identities of individuals or entities are legitimate, reducing the likelihood of fraud.
- Preventing Fraud Through Robust Identity Solutions: Fraudsters are becoming more sophisticated, exploiting gaps in traditional verification systems. By implementing dynamic and multi-layered identity solutions, businesses can stay ahead of threats and build customer trust.
Accurate identity verification protects organisations from reputational damage while fostering secure interactions in a digital-first era.
Account Verification
Account verification ensures that the details provided by customers or partners are accurate and valid. This process minimises risks associated with fraudulent accounts, payment failures, and operational inefficiencies.
- Account Validation Processes: These include validating bank account details, verifying the authenticity of contact information, and confirming the ownership of accounts. Businesses often use APIs and automated verification systems for seamless execution.
- Industry Best Practices for Secure Account Management:
- Implement multi-factor authentication (MFA) to strengthen security.
- Regularly audit accounts to detect and address irregularities.
- Use encryption to protect sensitive account data during transmission and storage.
By ensuring account integrity, businesses can reduce operational risks and improve customer satisfaction.
Digital Onboarding
Digital onboarding is the process of integrating new customers, employees, or partners into a system or service using digital tools. A well-designed onboarding process not only improves user experience but also mitigates risks associated with inaccurate data or weak authentication.
- Seamless and Secure Onboarding Processes for Businesses: Digital onboarding combines low-code workflows, automated identity verification, and real-time validation to make the onboarding experience efficient and secure. This reduces manual errors and accelerates the onboarding process.
- Reducing Risk Through Technological Innovations: Technologies like AI, machine learning, and blockchain have transformed onboarding. For example, AI can flag inconsistencies in submitted documents, while blockchain ensures data integrity. These innovations reduce the risk of onboarding fraudulent entities.
A streamlined digital onboarding process reflects a business’s commitment to security and efficiency, enhancing trust and long-term customer loyalty.
By integrating these elements—risk screening, due diligence, identity verification, account verification, and digital onboarding—organisations can create a comprehensive risk intelligence strategy. Each component addresses a specific layer of risk, collectively contributing to a safer, more resilient business ecosystem.
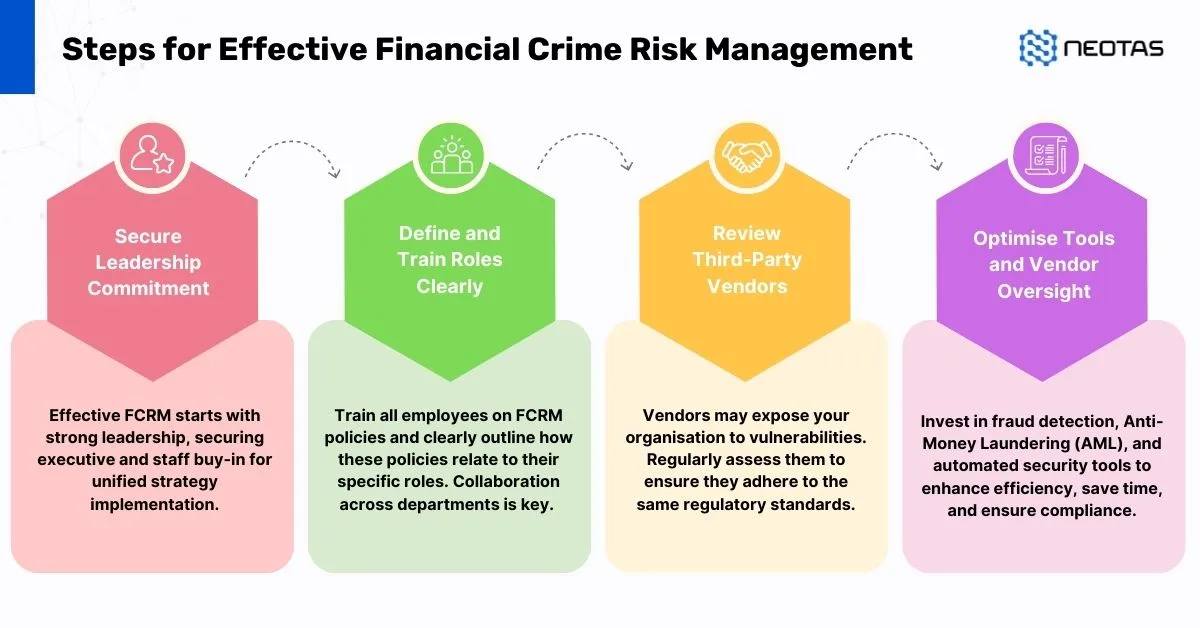
Developing an Effective Risk Intelligence Programme
An effective risk intelligence programme forms the backbone of proactive risk management for modern organisations. By combining advanced technologies, structured methodologies, and a forward-thinking approach, businesses can anticipate risks, mitigate them efficiently, and align their strategies with organisational objectives. The following elements—risk assessment, risk monitoring, and data collection—are critical for building a comprehensive risk intelligence framework.
Risk Assessment
Risk assessment is the cornerstone of any risk intelligence programme, providing insights into the likelihood and impact of potential threats. By identifying vulnerabilities, organisations can prioritise mitigation efforts and allocate resources effectively.
Types of Risk Assessments:
- Qualitative Assessments: Focus on descriptive analysis, relying on expert judgement and experience. These assessments are ideal for risks that are difficult to quantify, such as reputational threats.
- Quantitative Assessments: Use numerical data and statistical models to measure risk. This method is well-suited for financial risks, where probabilities and potential losses can be calculated.
- Hybrid Assessments: Combine qualitative and quantitative methods, offering a balanced approach for complex risk scenarios that require both subjective and data-driven analysis.
Tools and Technologies for Automating Risk Assessments:
- Risk Management Software: Platforms that integrate data collection, risk modelling, and reporting.
- Artificial Intelligence (AI): AI-driven tools analyse historical data and identify patterns to predict future risks.
- Scenario Simulation Software: Tools that simulate potential events, helping organisations understand risk impacts under various conditions.
Automating risk assessments not only enhances efficiency but also reduces the likelihood of human error, enabling organisations to make more informed decisions.
Sensing and Monitoring Risks
Real-time sensing and monitoring are essential for staying ahead of emerging threats. By leveraging advanced technologies, organisations can detect risks early and respond with agility.
Real-Time Risk Monitoring Techniques:
- Dashboards and Alerts: Centralised dashboards provide a consolidated view of risks, with automated alerts for high-priority issues.
- Continuous Monitoring: Integrating sensors, IoT devices, or software agents to track operational activities and flag anomalies in real time.
- Social Media and News Monitoring: Tracking social and media channels for trends, sentiment, or crises that may impact business operations.
These technologies enhance the speed and accuracy of risk detection, providing organisations with a significant strategic advantage.
Data Collection and Record Keeping
Comprehensive data collection and proper record-keeping are critical for building a robust risk intelligence programme. Reliable data serves as the foundation for accurate risk assessments, monitoring, and future planning.
Importance of Maintaining Comprehensive Risk Data:
- Informed Decision-Making: Access to historical and real-time data enables businesses to analyse trends and make evidence-based decisions.
- Compliance and Reporting: Many industries require organisations to maintain detailed risk records for audits and regulatory compliance.
- Trend Analysis and Improvement: Historical data helps identify recurring risks and measure the effectiveness of mitigation strategies.
Methods for Structuring and Storing Risk Data:
- Centralised Databases: Use cloud-based or on-premises databases to consolidate risk data from various sources.
- Standardised Formats: Maintain uniform data formats to ensure consistency and simplify analysis.
- Tagging and Metadata: Categorise data using tags or metadata to improve searchability and usability.
- Secure Backup Systems: Implement secure, redundant backup solutions to protect sensitive data against loss or breaches.
By organising and safeguarding their risk data, organisations ensure they are prepared for future challenges and equipped to refine their risk intelligence programmes continuously.
Integrating the Elements into a Risk Intelligence Programme
An effective risk intelligence programme is more than the sum of its parts. It requires seamless integration of risk assessment, monitoring, and data management into a unified strategy. When these elements work in harmony, organisations gain a comprehensive understanding of their risk landscape, enabling them to navigate uncertainties with confidence and precision.
Acting on Risk Intelligence
Risk intelligence is most effective when translated into actionable steps that guide decision-making and strategy. Acting on risk intelligence involves aligning insights with enterprise-level decisions, empowering teams through a blend of human expertise and technology, and strategically leveraging risk data to predict and prepare for future challenges.
Informed Decision-Making
Informed decision-making is the cornerstone of acting on risk intelligence. By aligning insights with organisational objectives, businesses can enhance their resilience and adaptability.
Aligning Risk Intelligence with Enterprise-Level Decisions:
Risk intelligence must feed directly into core business processes. For example:
- Strategic planning: Using risk insights to identify new markets or product lines.
- Operational adjustments: Adapting supply chains based on geopolitical or logistical risks.
- Compliance: Ensuring adherence to evolving regulatory requirements.Aligning risk intelligence ensures decisions are not made in isolation but are grounded in a comprehensive understanding of potential threats.
Examples of Data-Driven Risk Decisions:
- A financial institution using predictive analytics to avoid exposure to high-risk investments.
- A retailer adjusting inventory strategies based on supply chain risk forecasts.
- A healthcare provider improving cybersecurity measures after detecting vulnerabilities in patient data systems.
By integrating risk data into decision-making processes, organisations can make smarter, more sustainable choices.
Empowered Decision-Making
Empowered decision-making strikes a balance between leveraging advanced technologies and retaining human judgement. This approach ensures that risk intelligence serves as an enabler rather than a constraint.
Balancing Human Expertise with Technological Insights:
- Human expertise provides context, intuition, and ethical considerations that machines cannot replicate.
- Technological tools offer speed, accuracy, and the ability to process vast datasets.
Together, they form a complementary relationship where technology enhances human decision-making without replacing it.
Challenges of Over-Reliance on Automated Systems:
- Lack of Context: Algorithms may not fully understand the nuances of complex risks.
- False Positives/Negatives: Automated systems can misclassify risks, leading to either unnecessary action or missed threats.
- Technology Gaps: Over-reliance on automation can leave organisations vulnerable if systems fail or data is incomplete.
Maintaining a balance ensures organisations reap the benefits of technology while retaining the flexibility and critical thinking of human decision-makers.
Strategic Use of Risk Data
Strategic use of risk data transforms intelligence into long-term value. Organisations can use this data not only to address immediate risks but also to build a sustainable competitive advantage.
Incorporating Risk Intelligence into Business Strategy:
- Scenario Planning: Use risk data to simulate potential scenarios, helping organisations prepare for best- and worst-case outcomes.
- Resource Allocation: Prioritise investments in areas with the highest potential risk-reward balance.
- Growth Opportunities: Identify trends in risk data to uncover opportunities, such as expanding into markets with reduced regulatory risks.
Using Historical Risk Data to Predict Future Challenges:
- Historical data provides a baseline for understanding recurring risks and trends.
- Machine learning models can process this data to forecast future vulnerabilities and their likely impact.
- For example, a company that has experienced supply chain disruptions during specific seasonal events can prepare alternative sourcing strategies in advance.
Strategically leveraging risk data not only protects businesses from threats but also positions them for long-term success.
Integrating Actionable Risk Intelligence
To act effectively on risk intelligence, organisations must ensure that insights flow seamlessly into their decision-making and strategic planning processes. This requires:
- Clear communication of risk insights across teams and departments.
- A balanced reliance on technology and human judgement.
- A commitment to continuously refining and evolving risk intelligence practices.
By embedding risk intelligence into their operational fabric, businesses can make decisions that are not only informed but also strategic, resilient, and forward-looking.
Advanced Topics in Risk Intelligence
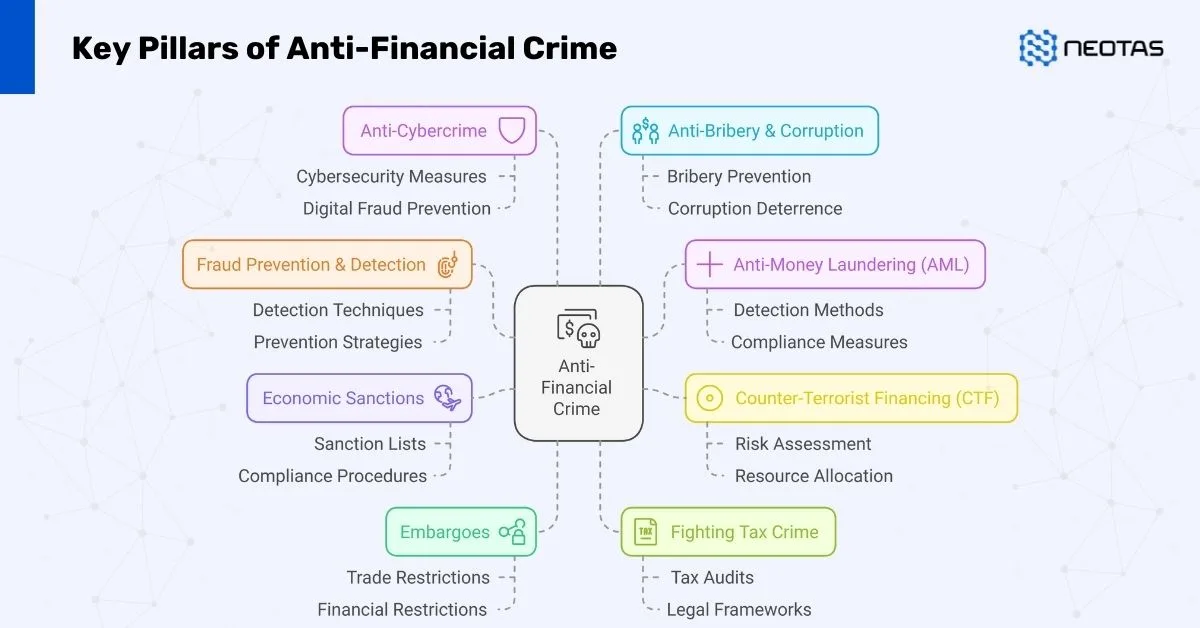
As the complexity of the global business environment continues to increase, risk intelligence has evolved into a highly sophisticated field. Beyond traditional risk management practices, modern approaches incorporate advanced methodologies, technology, and human expertise to address financial crime compliance, third-party risks, and emerging global trends. This integration empowers organisations to adapt to challenges with agility and precision, ensuring resilience and long-term success.
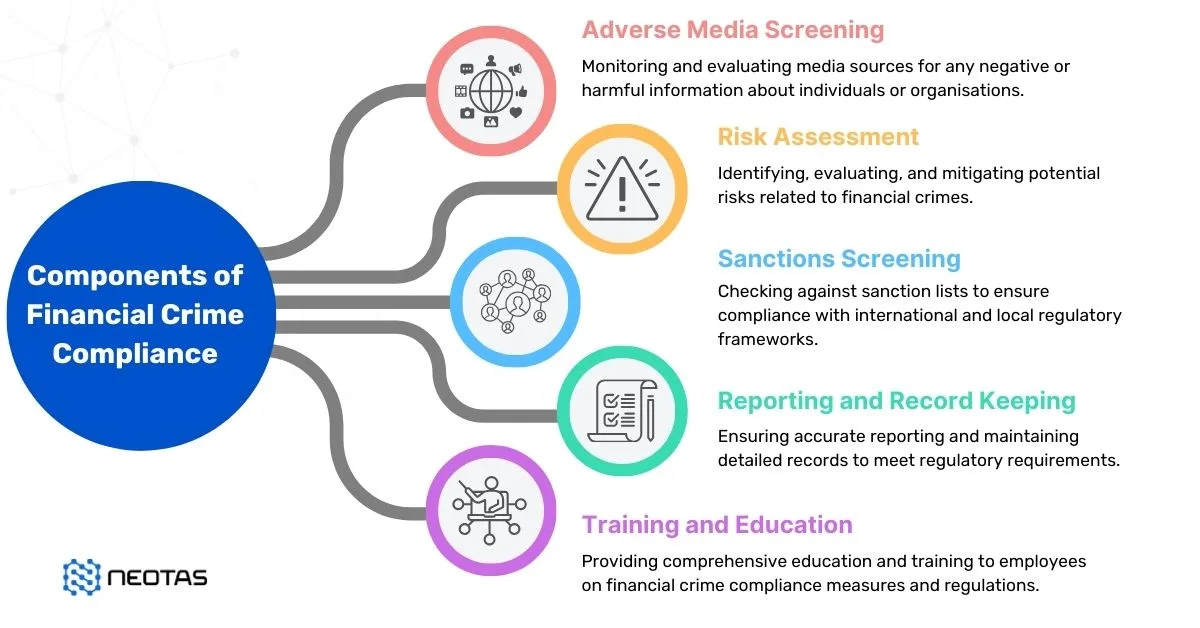
Financial Crime Compliance
Overview of Financial Crime Risks and Compliance Requirements
Financial crime remains a critical concern for businesses, with risks including money laundering, fraud, terrorist financing, and tax evasion. These threats can lead to significant financial losses, regulatory penalties, and reputational damage if not addressed effectively. To counter these risks, organisations must comply with a range of regulations, such as the UK’s Money Laundering Regulations, the Financial Action Task Force (FATF) guidelines, and GDPR for data protection.
Key compliance requirements include:
- Know Your Customer (KYC) protocols to verify customer identities and ensure legitimacy.
- Transaction Monitoring Systems to detect suspicious financial activity in real time.
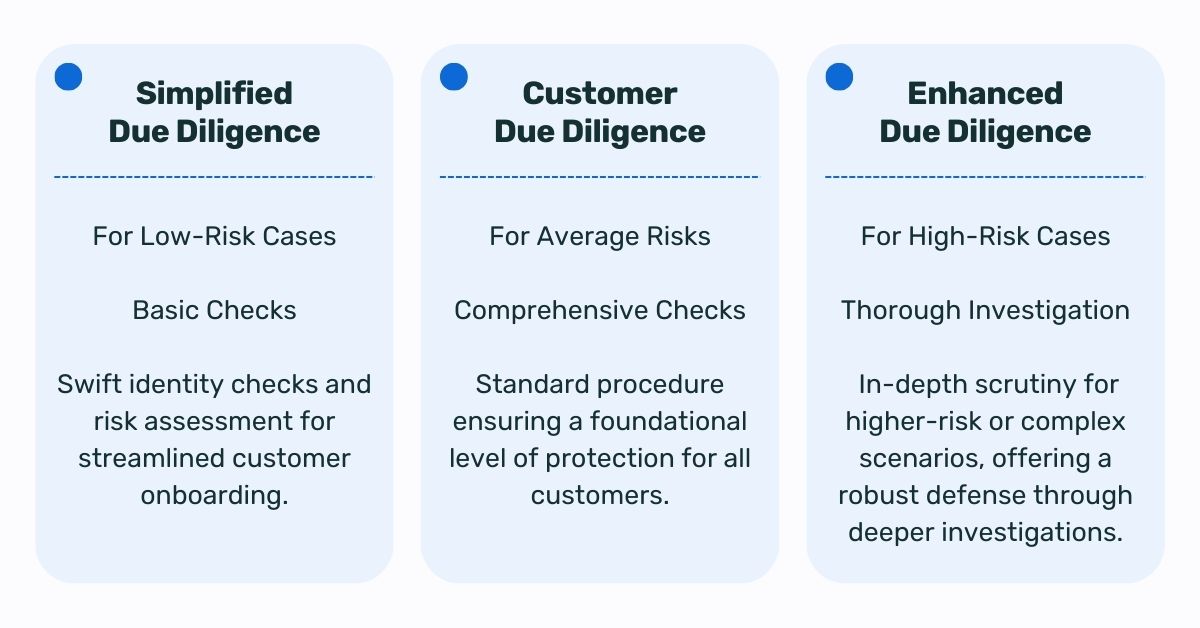
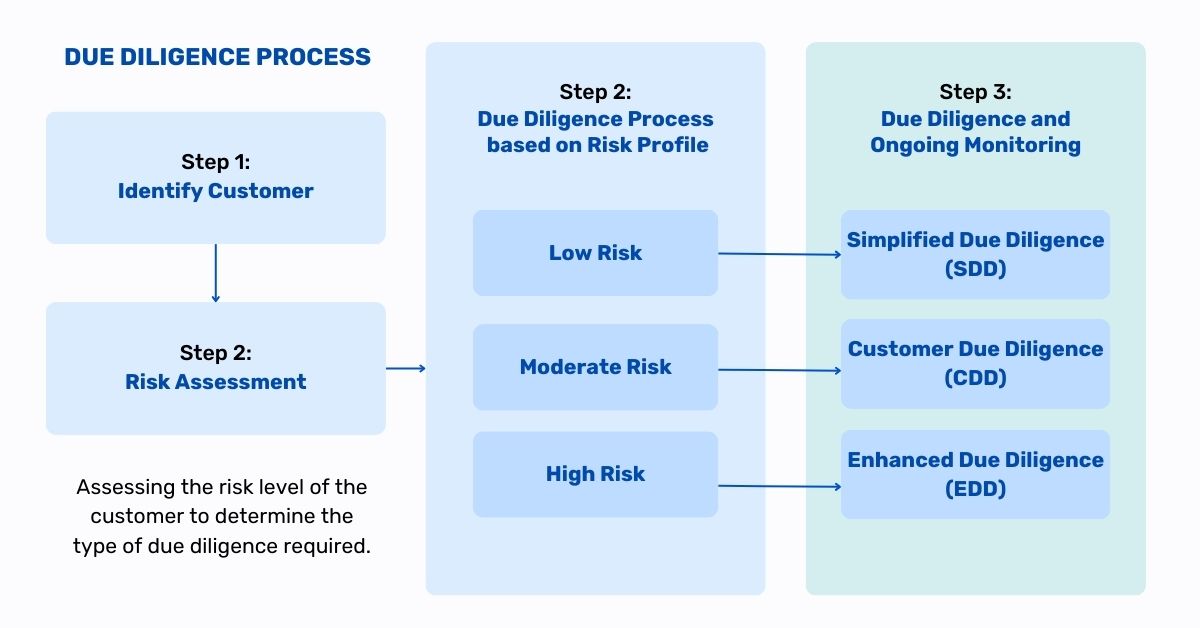
- Enhanced Due Diligence (EDD) for high-risk customers and transactions.
Compliance demands are continuously evolving, requiring businesses to stay up-to-date with regulatory changes and implement robust systems that align with both local and international standards.
Future Trends in Financial Crime Prevention
Financial crime prevention is undergoing rapid transformation, driven by advancements in technology and data analytics. Key trends include:
- AI-Powered Detection: Artificial intelligence is being used to identify patterns in transaction data, enabling early detection of anomalies and fraud.
- Blockchain Transparency: Distributed ledger technology offers secure, transparent transaction records, reducing the risk of tampering and fraud.
- Regulatory Technology (RegTech): Automation tools are simplifying compliance processes, reducing costs while enhancing accuracy.Organisations that adopt these innovations will be better positioned to stay compliant and mitigate financial crime risks.
Read More on Financial Crime Compliance
Download the Financial Crime Compliance Trends Report
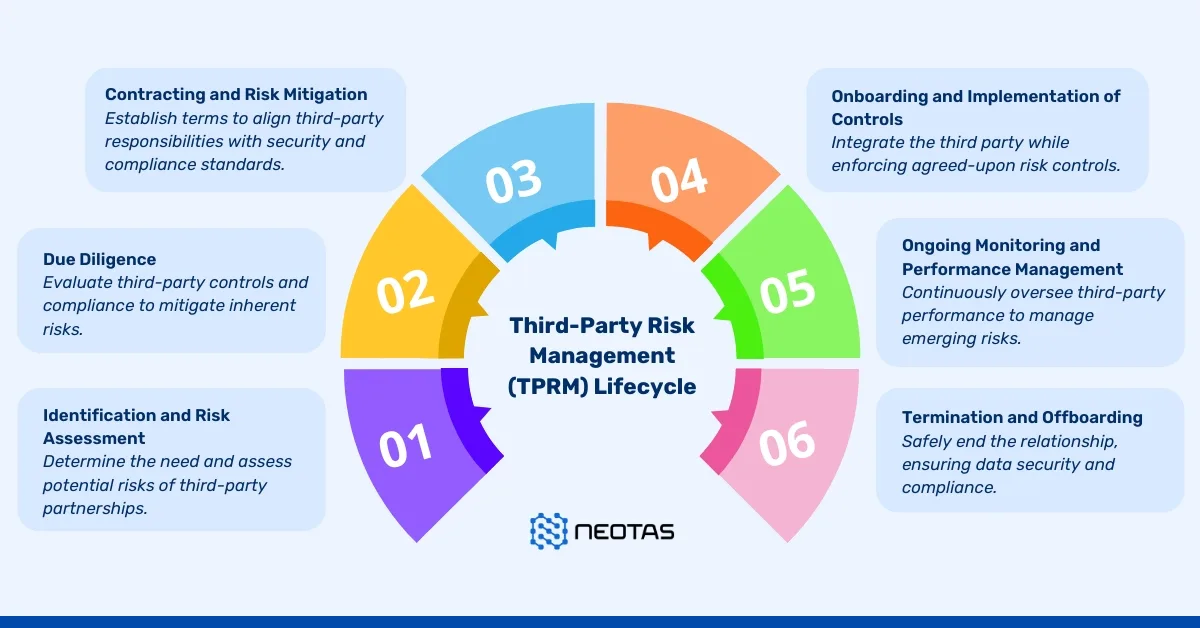
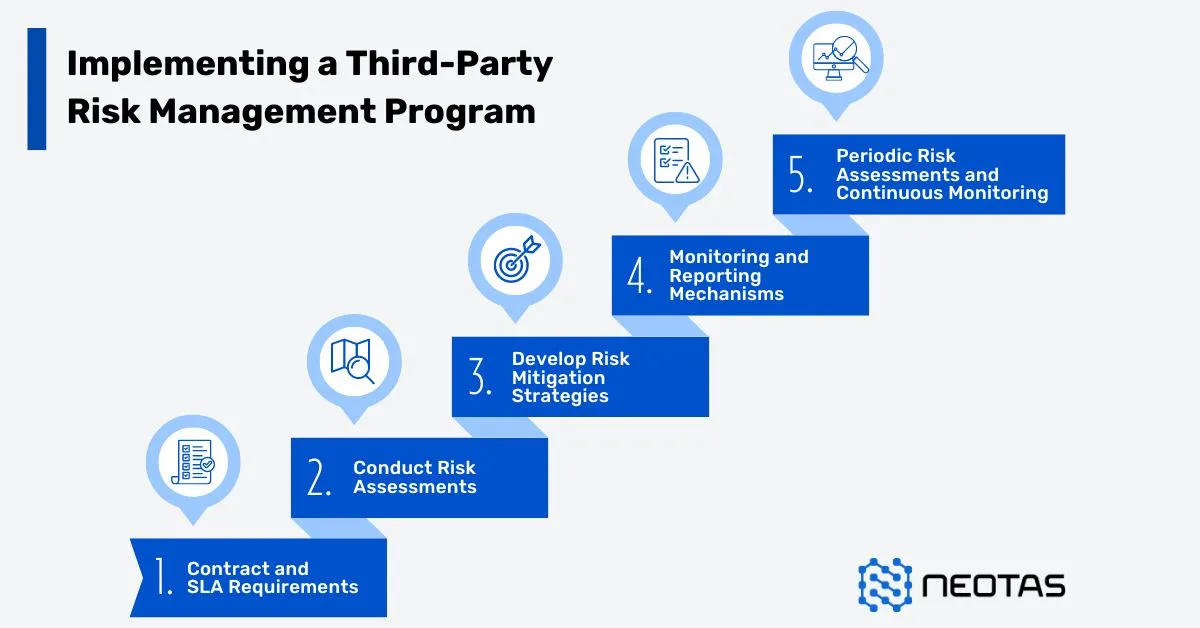
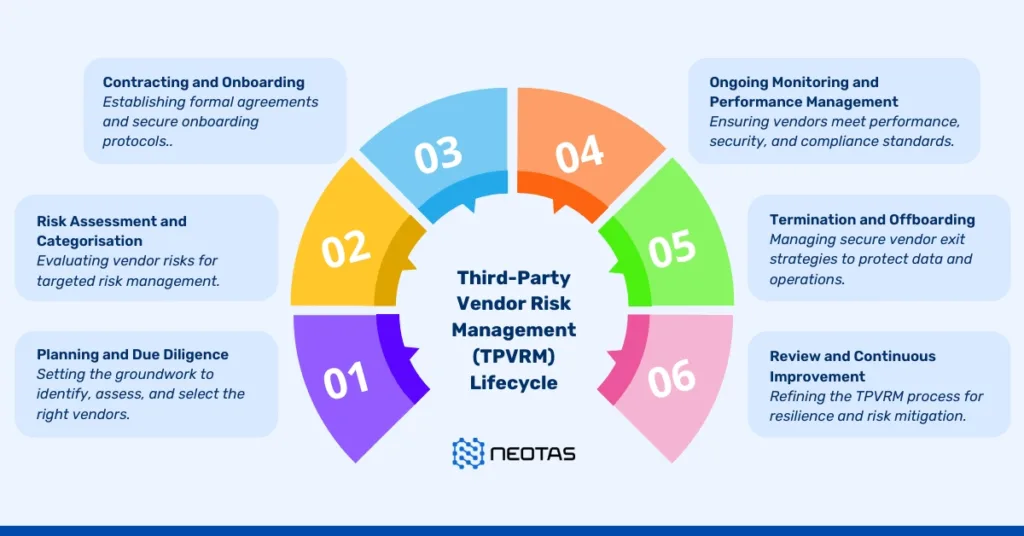
Third-Party Risk Management (TPRM)
Identifying and Mitigating Risks Posed by Vendors, Partners, and Suppliers
Third-party risk management (TPRM) is critical as organisations increasingly rely on external vendors, partners, and suppliers. These relationships introduce potential risks, including operational disruptions, data breaches, and non-compliance with regulations.
Steps to mitigate these risks include:
- Initial Due Diligence: Thoroughly vetting third parties during onboarding to assess financial stability, ethical practices, and regulatory compliance.
- Continuous Monitoring: Using automated systems to track third-party activities and flag potential risks.
- Contractual Safeguards: Including clauses in agreements that outline compliance requirements and consequences for breaches.
Building a Competitive Advantage Through Proactive Third-Party Management
Proactively managing third-party risks not only mitigates threats but also provides strategic benefits:
- Enhanced Reputation: Partnering with ethical and compliant third parties reinforces brand trust.
- Operational Continuity: Anticipating and mitigating disruptions ensures seamless operations.
- Cost Savings: Early identification of risks prevents costly incidents, such as supply chain breakdowns or regulatory fines.
Organisations that excel in TPRM can create a competitive edge, demonstrating responsibility and reliability to stakeholders.
Read More on Third-Party Risk Management (TPRM) Lifecycle, Third-Party Risk and Best Practices for TPRM Implementation
Emerging Risks and Trends
The Role of Climate Change and Natural Disasters in Shaping Risk Landscapes
Climate change is a growing concern for businesses, with risks ranging from extreme weather events to regulatory shifts aimed at reducing carbon emissions. These risks can disrupt supply chains, damage infrastructure, and increase operational costs.
To address these challenges, businesses should:
- Integrate Climate Risk into Strategy: Conduct scenario analyses to assess the impact of climate-related risks.
- Invest in Resilience: Strengthen infrastructure and diversify supply chains to mitigate the effects of natural disasters.
- Commit to Sustainability: Adopt environmentally responsible practices to align with regulatory and stakeholder expectations.
Adapting to Political and Regulatory Changes
The global political and regulatory environment is in constant flux, influenced by geopolitical tensions, trade wars, and evolving compliance standards. Businesses must:
- Monitor Developments: Stay informed about changes in regulations affecting key markets.
- Foster Flexibility: Build strategies that can adapt to sudden shifts in trade policies or political stability.
- Engage with Stakeholders: Maintain open communication with regulators and partners to navigate uncertainties effectively.
Emerging risks demand agility and foresight, making proactive adaptation a cornerstone of modern risk intelligence.
Read More on Managing risk with suppliers and third parties using open-source intelligence (OSINT)
Leveraging Technology for Risk Intelligence
Automating Risk Processes
Benefits of Automation in Risk Assessments and Monitoring
Automation plays a transformative role in risk intelligence by:
- Enhancing Efficiency: Automated tools process vast datasets quickly, identifying risks in real time.
- Reducing Errors: Algorithms minimise human error, ensuring consistent and accurate analysis.
- Freeing Resources: By handling routine tasks, automation allows teams to focus on strategic decisions.
Tools for Risk Management Automation
- AI-Powered Platforms: Predictive analytics and machine learning for real-time risk detection.
- Robotic Process Automation (RPA): Automating repetitive compliance tasks, such as data validation.
- Integrated Dashboards: Consolidating risk data for streamlined reporting and decision-making.
Artificial Intelligence Risk Management
How Artificial Intelligence Transforms Risk Intelligence
AI enhances risk intelligence by uncovering patterns and trends that are often invisible to human analysts. It excels in areas such as anomaly detection, predictive modelling, and sentiment analysis, providing actionable insights that empower organisations to act swiftly.
Use Cases of AI in Risk Detection and Mitigation
- Fraud Prevention: Identifying suspicious activities in financial transactions.
- Supply Chain Optimisation: Predicting disruptions and recommending contingency plans.
- Cybersecurity: Detecting and neutralising threats before they escalate.
Digital Transformation in Risk Management
Impacts of Digital Technologies on Traditional Risk Practices
Digital technologies, such as cloud computing, blockchain, and IoT, have revolutionised risk management by enabling real-time insights and scalable solutions. Traditional processes that were once manual and time-intensive are now streamlined and data-driven.
Adopting New Technologies for Competitive Risk Management
Businesses that adopt digital transformation gain a competitive edge by:
- Improving Agility: Responding to risks faster with real-time monitoring.
- Enhancing Data Security: Leveraging blockchain for tamper-proof records.
- Reducing Costs: Automating workflows to improve efficiency and scalability.
The Role of Human Expertise in Risk Intelligence
Balancing Human Insights with Automated Systems
While technology enhances efficiency, human expertise remains indispensable for interpreting complex risks. Automated systems may identify anomalies, but understanding the context and ethical implications requires human judgement.
The Importance of Expertise in Interpreting Complex Risks
- Contextual Analysis: Human experts provide nuanced understanding of risks influenced by cultural, geopolitical, or industry-specific factors.
- Strategic Thinking: Decision-makers align risk strategies with broader organisational goals.
- Ethical Oversight: Humans ensure that actions are ethically sound, especially in ambiguous scenarios.
Industry-Specific Risk Intelligence Applications
Risk intelligence is not a one-size-fits-all approach; its application varies across industries depending on unique challenges and operational landscapes. Industries such as financial services, healthcare, technology, and manufacturing leverage tailored risk intelligence strategies to mitigate threats, ensure compliance, and drive resilience.
Risk Intelligence for Financial Services
The financial services sector faces a broad spectrum of risks, including regulatory compliance, fraud, market volatility, and cybersecurity. Risk intelligence is critical for maintaining trust and stability in this highly regulated and fast-moving industry.
Applications:
- Financial Crime Compliance: Implementing risk intelligence tools to detect money laundering, fraud, and insider trading. AI-powered systems analyse transaction patterns in real-time, flagging suspicious activities for review.
- Market Risk Management: Leveraging predictive analytics to anticipate market fluctuations, enabling informed investment decisions.
- Regulatory Compliance: Automated tools ensure adherence to dynamic global regulations such as MiFID II, FATCA, and GDPR, reducing the risk of fines and reputational damage.
- Customer Due Diligence (CDD): Advanced risk intelligence platforms streamline KYC processes, improving onboarding times and compliance accuracy.
Read more on Customer Due Diligence requirements
Risk Intelligence for Healthcare
The healthcare industry faces unique risks, including patient data breaches, regulatory non-compliance, and supply chain disruptions. Risk intelligence ensures not only the protection of sensitive data but also the efficient delivery of critical services.
Applications:
- Data Privacy and Cybersecurity: Risk intelligence systems monitor healthcare networks for vulnerabilities, ensuring compliance with regulations such as the GDPR and HIPAA.
- Supply Chain Management: Real-time risk monitoring helps hospitals manage pharmaceutical and medical supply chains, avoiding critical shortages.
- Clinical Trials Risk Management: Advanced analytics identify potential risks in clinical trials, such as participant safety concerns or data inconsistencies.
- Regulatory Compliance: Automated solutions track evolving healthcare regulations, ensuring compliance without overburdening administrative staff.
Risk Intelligence for Technology
Technology companies operate in a fast-paced environment where risks such as intellectual property theft, regulatory challenges, and cybersecurity breaches are prevalent. Risk intelligence allows organisations to navigate these challenges while driving innovation.
Applications:
- Cybersecurity Risk Mitigation: AI-powered risk intelligence tools monitor for potential data breaches and malicious activities, offering real-time alerts and response strategies.
- Intellectual Property Protection: Risk intelligence platforms help identify and prevent unauthorised use of proprietary technologies or trademarks.
- Regulatory Adaptation: Tools monitor global tech regulations, ensuring compliance in areas such as data privacy and AI governance.
- Innovation Risk Assessment: Risk intelligence evaluates the potential pitfalls of new technologies, enabling organisations to plan for disruptions and optimise R&D investments.
Supply Chain Risk Intelligence
The manufacturing and supply chain industry faces risks such as production delays, raw material shortages, geopolitical disruptions, and regulatory non-compliance. Risk intelligence provides the insights needed to ensure continuity and efficiency.
Applications:
- Supply Chain Visibility: Real-time risk monitoring tools track suppliers, logistics, and geopolitical risks, enabling contingency planning.
- Operational Risk Management: Risk intelligence identifies vulnerabilities in production lines, such as equipment failures or workforce shortages.
- Sustainability and Compliance: Tools monitor compliance with environmental standards, ensuring adherence to regulations such as the UK’s Modern Slavery Act.
- Geopolitical Risk Mitigation: Predictive analytics assess political instability in key sourcing regions, allowing businesses to diversify suppliers or stockpile critical resources.
Across all sectors, adopting tailored risk intelligence solutions enables organisations to navigate uncertainties, enhance efficiency, and maintain a competitive edge.
FAQs on Risk Intelligence
What is Risk Intelligence?
Risk Intelligence refers to an organisation’s ability to identify, assess, and mitigate risks across all operational levels. It combines data-driven insights, advanced analytics, and human expertise to enable informed decision-making. This approach focuses on proactive management of uncertainties, helping organisations respond effectively to emerging threats. Risk Intelligence plays a vital role in building resilience by integrating risk management into strategic planning and day-to-day operations, ensuring that businesses remain agile and competitive in a rapidly evolving global landscape.
What does a Risk Intelligence Analyst do?
A Risk Intelligence Analyst is responsible for monitoring, assessing, and reporting on potential risks that could impact an organisation. They gather and analyse data from various sources, use predictive models to forecast threats, and collaborate with stakeholders to implement risk mitigation strategies. Their expertise spans areas such as financial risks, cybersecurity, compliance, and supply chain vulnerabilities. By providing actionable insights, Risk Intelligence Analysts enable organisations to make informed decisions, enhancing resilience and competitive advantage.
What are the 3 main types of risk?
The three main types of risk are Operational Risk, Financial Risk, and Strategic Risk:
- Operational Risk: Involves disruptions in internal processes, systems, or resources.
- Financial Risk: Relates to market volatility, credit issues, or liquidity constraints.
- Strategic Risk: Arises from poor decision-making or external factors affecting long-term goals.
Understanding these risk types allows organisations to prioritise mitigation strategies and allocate resources effectively.
How to take intelligent risks?
Taking intelligent risks involves balancing potential rewards with well-informed decisions. This process starts with thorough risk assessment, leveraging tools like Risk Intelligence software to evaluate the likelihood and impact of uncertainties. Organisations should employ predictive analytics and scenario modelling to foresee outcomes and develop mitigation plans. Engaging cross-functional teams for diverse perspectives ensures a comprehensive understanding of risks. By aligning risks with strategic goals, businesses can innovate and grow while safeguarding their core operations.
What is Risk Intelligence Software?
Risk Intelligence Software is a technology platform that helps organisations identify, monitor, and mitigate risks. These tools use advanced analytics, artificial intelligence, and machine learning to process vast amounts of data and provide actionable insights. Features often include real-time monitoring, compliance tracking, and risk scoring. By automating assessments and delivering timely alerts, Risk Intelligence Software supports proactive decision-making, reducing the likelihood of financial, operational, and reputational losses.
What software is used for risk management?
Several software solutions cater to risk management needs, including platforms like Archer, MetricStream, and Resolver. These tools offer comprehensive features such as risk assessment, compliance tracking, and incident management. Many include integrations with data sources for enhanced analysis and reporting. Advanced options incorporate AI and machine learning to detect emerging threats and automate processes. Selecting the right software depends on organisational requirements, industry regulations, and scalability needs.
What is the Risk Intelligence Model?
The Risk Intelligence Model is a framework that guides organisations in systematically identifying and managing risks. It encompasses three key stages: Assessment, where potential threats are identified; Monitoring, which involves real-time tracking of risk indicators; and Response, focusing on mitigation and resolution strategies. This model helps businesses align their risk management efforts with strategic objectives, enhancing resilience and agility in an unpredictable environment.
Can AI do risk management?
Yes, AI has become a transformative force in risk management. By analysing vast datasets, AI identifies patterns and predicts potential risks with remarkable accuracy. AI-driven tools can automate processes such as fraud detection, compliance monitoring, and supply chain risk assessments. Furthermore, machine learning algorithms adapt to new data, improving their efficiency over time. While AI significantly enhances risk management, human oversight remains essential to interpret insights and make nuanced decisions.
What are examples of software risks?
Software risks can arise from various sources, including:
- Security Risks: Vulnerabilities that may be exploited by cybercriminals.
- Performance Risks: System failures or lags affecting user experience.
- Compliance Risks: Failure to adhere to regulatory standards, such as GDPR.
Mitigating software risks requires robust development practices, thorough testing, and continuous monitoring to ensure the software performs as intended while remaining secure.
Can ChatGPT generate risk assessments?
ChatGPT can support risk assessments by analysing data, summarising risk factors, and generating preliminary reports. While it is not a substitute for dedicated Risk Intelligence tools, it can assist in scenario modelling, brainstorming potential risks, and drafting mitigation strategies. However, its outputs should be validated by experts to ensure accuracy and alignment with organisational objectives.
Can AI predict risk?
Yes, AI excels at predicting risks by processing vast datasets and identifying patterns that might elude human analysis. Predictive models powered by machine learning anticipate potential threats, such as financial fraud, supply chain disruptions, or cybersecurity breaches. These insights enable organisations to implement timely mitigation strategies, transforming risk management from a reactive to a proactive discipline.
What is a Risk Intelligence Analyst?
A Risk Intelligence Analyst is a professional specialising in evaluating and managing risks. They use analytical tools and techniques to assess financial, operational, and strategic risks, and they develop actionable insights to guide decision-making. By identifying vulnerabilities and forecasting threats, they play a crucial role in safeguarding an organisation’s assets and reputation.
What is the 3 risk model?
The 3 risk model refers to three approaches to managing risk:
- Avoidance: Eliminating activities that pose significant risks.
- Reduction: Minimising the likelihood or impact of risks.
- Transfer: Shifting risks to third parties, such as through insurance or outsourcing.
Each approach should align with the organisation’s overall risk tolerance and strategic goals.
What is AML Risk Rating Model?
The AML (Anti-Money Laundering) Risk Rating Model evaluates customer risks based on factors such as geographic location, transaction history, and business type. It assigns risk scores to help organisations comply with AML regulations, ensuring effective detection and prevention of financial crimes.
What are the top 5 risk categories?
The top five risk categories are:
- Financial Risk: Includes credit, market, and liquidity risks.
- Operational Risk: Relates to system failures or process inefficiencies.
- Compliance Risk: Stems from regulatory violations.
- Strategic Risk: Associated with poor decision-making or market changes.
- Reputational Risk: Impacts public perception and trust.
What is the Risk Intelligence Score?
The Risk Intelligence Score is a metric that quantifies an organisation’s exposure to risk, providing a snapshot of its resilience. It is calculated based on factors such as vulnerability, mitigation strategies, and historical incidents. This score enables stakeholders to benchmark and improve their risk posture.
What is the full form of RCSA Risk?
RCSA stands for Risk Control Self-Assessment, a process where organisations identify and evaluate risks, controls, and potential gaps. It helps in prioritising mitigation efforts and aligning risk management with business objectives.
What is Risk IQ?
Risk IQ refers to the level of awareness and understanding an organisation has about its risk landscape. It also refers to tools and platforms offering advanced threat intelligence, enabling businesses to anticipate and mitigate risks effectively.
What is HIRA Score?
The HIRA Score, or Hazard Identification and Risk Assessment Score, evaluates the severity and likelihood of risks, particularly in occupational safety and environmental contexts. It is a critical metric for compliance and proactive risk management.
What is AML Risk Score?
The AML risk score is a metric used by financial institutions to evaluate the potential risk associated with money laundering activities. It takes into account factors like the customer’s geographic location, industry, transaction patterns, and historical behaviour. A higher AML risk score indicates increased scrutiny is needed, helping organisations meet compliance requirements while preventing financial crimes. These scores are essential for maintaining regulatory standards and safeguarding the organisation from reputational and financial harm.
What is KYC Risk Classification?
KYC (Know Your Customer) risk classification is the process of categorising customers based on the level of risk they pose. Factors such as geographic location, nature of business, and transactional behaviours are considered. Customers are typically classified as low, medium, or high risk, allowing organisations to allocate resources for due diligence accordingly. Proper classification ensures compliance with regulatory requirements and helps prevent fraud and financial crimes.
What are the 4 types of risk assessment?
Risk assessments come in four main types: qualitative, quantitative, dynamic, and hybrid.
- Qualitative assessments focus on descriptive analysis, often using scenarios and expert opinions.
- Quantitative methods rely on numerical data and statistical models to evaluate risk.
- Dynamic assessments are adaptive, evolving in response to real-time data.
- Hybrid approaches combine qualitative and quantitative elements, providing a balanced view of risks.
Each type has its use case depending on organisational needs and the complexity of the risk landscape.
What is a Threat Intelligence Tool?
Threat intelligence tools are software solutions designed to collect and analyse data on potential threats, particularly in cybersecurity. These tools monitor dark web activity, malicious IP addresses, and other indicators of compromise to provide actionable insights. By enabling organisations to detect and respond to threats proactively, these tools reduce the likelihood of breaches and enhance overall security posture.
What is Risk Control Tool?
Risk control tools are frameworks, technologies, or practices used to manage and mitigate risks effectively. These can include software for compliance monitoring, automated workflows for incident management, and training programmes to enhance employee awareness. By integrating these tools into daily operations, organisations can identify vulnerabilities early and respond to risks efficiently.
What is Risk Sensing?
Risk sensing is the practice of using advanced analytics and AI to detect emerging risks before they materialise. It involves monitoring internal and external data sources, such as market trends, social media, and regulatory changes, to identify potential threats. Organisations that implement risk sensing capabilities gain a competitive advantage by staying ahead of disruptions and making informed strategic decisions.
What are the 3 C’s of Risk?
The 3 C’s of risk—Context, Culture, and Capability—form a framework for understanding and managing organisational risks.
- Context refers to the environment in which risks arise, including internal and external factors.
- Culture is the organisational attitude towards risk, including leadership and employee behaviours.
- Capability denotes the tools, expertise, and resources available to address risks.
Together, these elements provide a holistic view of an organisation’s risk readiness.
What is Risk Consulting Services?
Risk consulting services help organisations enhance their risk management practices by providing expert guidance, tools, and tailored strategies. These services typically cover areas such as compliance, operational risk, cybersecurity, and third-party risk. By leveraging industry expertise, consulting services empower businesses to mitigate threats, optimise processes, and build resilience in an increasingly complex world.
What is Risk Intelligence Services?
Risk intelligence services provide businesses with actionable insights and tools to identify, assess, and mitigate risks across their operations. These services often combine technology platforms, expert analysis, and real-time data to deliver comprehensive solutions. From financial crime compliance to supply chain risk management, they ensure organisations are equipped to navigate uncertainties effectively while maintaining competitive advantage.
What is the full form of IRM?
IRM stands for Integrated Risk Management, a holistic approach that combines multiple risk management disciplines into a unified framework. Unlike traditional risk management, IRM focuses on strategic alignment, ensuring risks are managed in line with business objectives. This method enhances decision-making and fosters organisational resilience.
What is IAM Risk?
IAM (Identity and Access Management) risk pertains to vulnerabilities in managing user identities and access permissions within an organisation. Improperly configured IAM systems can lead to unauthorised access, data breaches, and compliance violations. Mitigating IAM risk involves implementing robust authentication protocols, regular access reviews, and continuous monitoring to ensure security and compliance.
What is TRI in Cybersecurity?
TRI in cybersecurity refers to Threat, Risk, and Impact. This framework helps organisations evaluate security risks by assessing the likelihood of a threat, the risk it poses to assets, and the potential impact if realised. Understanding TRI enables organisations to prioritise their cybersecurity efforts and allocate resources effectively.
What is the full form of TRI?
In various contexts, TRI can stand for Threat-Risk-Impact in cybersecurity or Total Risk Index in broader risk analysis frameworks. Both interpretations focus on evaluating risks holistically, enabling organisations to address vulnerabilities effectively and strategically.
What are the 3 C’s of Cybersecurity?
The 3 C’s of cybersecurity—Confidentiality, Integrity, and Availability—are fundamental principles that guide security strategies.
- Confidentiality ensures sensitive data is accessible only to authorised parties.
- Integrity protects data from unauthorised modifications.
- Availability ensures that systems and data are accessible when needed.
These principles form the foundation of robust cybersecurity frameworks.
Tags: risk intelligence, artificial intelligence risk management, artificial intelligence risk management framework, risk intelligence software, risk intelligence platform, supply chain risk intelligence, cyber risk intelligence, advanced risk intelligence solutions, what is risk intelligence, business risk intelligence, third party risk intelligence, artificial intelligence for risk management, predictive risk intelligence, country risk intelligence, risk management intelligence, climate risk intelligence, risk intelligence solutions, business intelligence solutions, risk intelligence analyst, risk intelligence data, supply chain risk intelligence



 WHAT WE OFFER
WHAT WE OFFER AML Case Studies:
AML Case Studies: Schedule a Call
Schedule a Call


















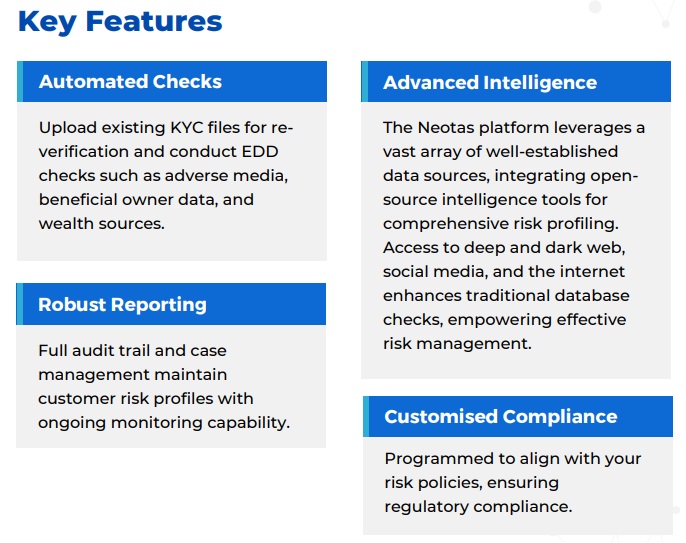
 Identify high-risk customers, transactions, and business relationships.
Identify high-risk customers, transactions, and business relationships. Strengthen regulatory compliance.
Strengthen regulatory compliance.






















 Economic Forecasting – Analysing global financial trends to prepare for inflation, interest rate changes, and recessions.
Economic Forecasting – Analysing global financial trends to prepare for inflation, interest rate changes, and recessions. Regulatory Trend Analysis – Monitoring upcoming laws and regulations to adjust compliance frameworks.
Regulatory Trend Analysis – Monitoring upcoming laws and regulations to adjust compliance frameworks. Geopolitical Risk Assessments – Identifying supply chain risks caused by international trade restrictions, political instability, or sanctions.
Geopolitical Risk Assessments – Identifying supply chain risks caused by international trade restrictions, political instability, or sanctions. Competitive Benchmarking – Studying market trends to refine pricing strategies and product development.
Competitive Benchmarking – Studying market trends to refine pricing strategies and product development. Identifying risks before they escalate.
Identifying risks before they escalate.