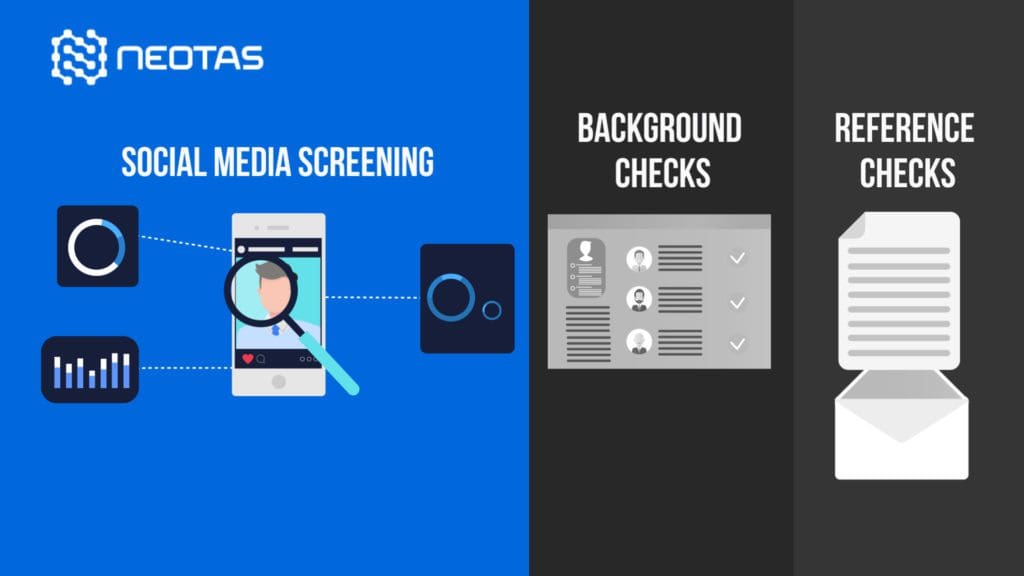
TPRM Methodology
Comprehensive Guide to Third-Party Risk Management (TPRM) Methodology – Learn how to effectively manage third-party risks in 2025 with our comprehensive guide on Third-Party Risk Management (TPRM), covering key components, best practices, and common challenges in TPRM Methodology.
The modern business ecosystem is deeply interconnected, with organisations increasingly depending on third-party vendors to optimise operations, reduce costs, and enhance service delivery. However, these relationships come with their risks. Third-Party Risk Management (TPRM) methodology is critical to mitigate potential threats, ensure compliance, and safeguard organisational assets. This guide explores the intricacies of the TPRM methodology, providing actionable insights for effective implementation.
What is Third-Party Risk Management (TPRM) Methodology?
TPRM methodology refers to a systematic approach to identifying, assessing, mitigating, and monitoring risks associated with engaging third-party vendors. These risks may stem from cybersecurity vulnerabilities, regulatory non-compliance, operational disruptions, or reputational harm. A robust TPRM methodology integrates these risk considerations into every stage of the vendor lifecycle.
Why is TPRM Essential?
Third-party risks are multifaceted and can arise at any stage of a business relationship. Common risk categories include:
- Cybersecurity Risks: Vendors with inadequate security measures can become entry points for cyberattacks, compromising sensitive data.
- Compliance Risks: Non-compliance with legal and regulatory requirements by vendors can expose organisations to fines and reputational damage.
- Operational Risks: Vendor failures can disrupt supply chains, affect service delivery, and harm business operations.
- Reputational Risks: Associations with unethical or irresponsible vendors can tarnish an organisation’s public image.
By implementing a robust TPRM methodology, organisations can minimise these risks while maintaining productive partnerships.
Key Components of Third-Party Risk Management (TPRM) Methodology
A robust TPRM methodology is essential for effectively managing the risks associated with third-party relationships. By adopting a systematic approach, organisations can not only safeguard their operations but also strengthen vendor relationships. Below, we delve deeper into the essential components of a well-designed TPRM methodology, ensuring a clear understanding of each element’s significance.
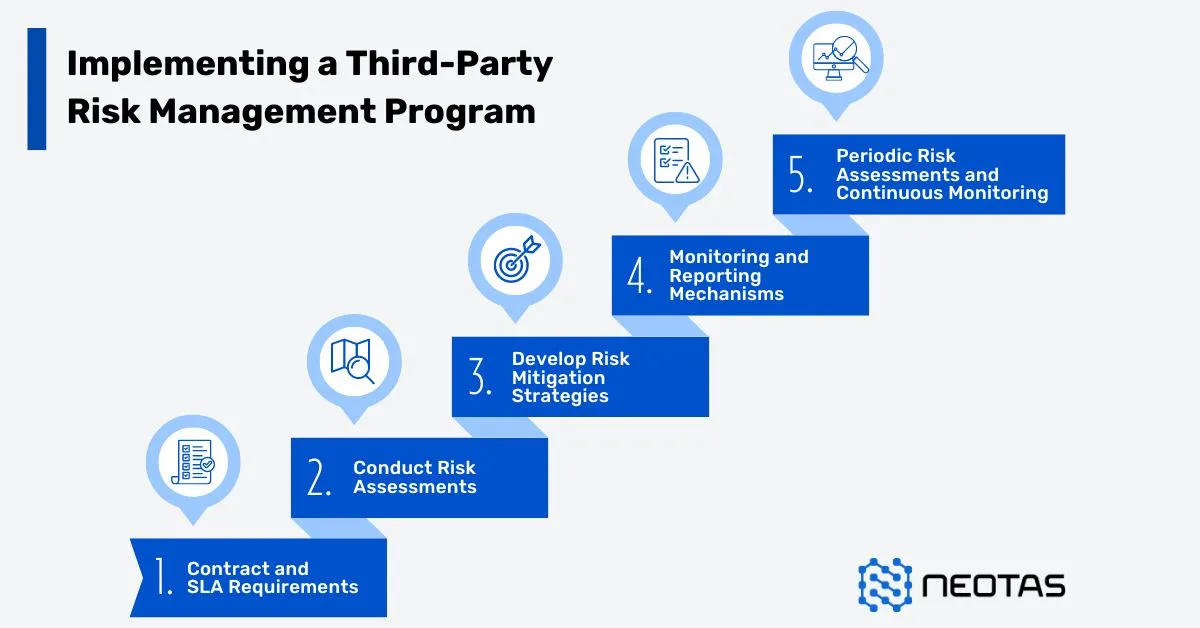
1. Vendor Identification and Classification
To manage third-party risks effectively, organisations must first establish a comprehensive view of their vendor ecosystem.
- Create a Centralised Vendor Database
A central repository of all third-party relationships is critical. This database should detail vendor information, including the services they provide, the systems they access, and the data they handle. Having this visibility ensures that no vendor falls outside the purview of the risk management framework. - Classify Vendors by Risk
Not all vendors pose the same level of risk. Categorising vendors allows organisations to allocate resources proportionally. Examples include:- High-risk vendors: Vendors with access to sensitive data, critical systems, or those integral to operational continuity.
- Low-risk vendors: Vendors providing non-critical services, such as office supplies, with minimal impact on the business.
This classification ensures targeted risk management and resource efficiency.
2. Risk Assessment and Due Diligence
Risk assessment forms the backbone of any TPRM methodology. It is vital to evaluate potential vulnerabilities associated with each third-party relationship.
- Initial Risk Assessment
Begin by assessing each vendor’s overall risk profile. This includes their:- Financial stability to ensure reliability and longevity.
- Compliance history to identify any prior regulatory violations.
- Security measures to understand their capability to protect sensitive data.
- Enhanced Due Diligence
For vendors categorised as high-risk, a more in-depth evaluation is necessary. This includes:- Cybersecurity Audits: Assess the vendor’s IT infrastructure, data protection practices, and incident response capabilities.
- Regulatory Compliance Verification: Ensure vendors comply with industry-specific regulations, such as GDPR or FCA standards.
- Reputation Analysis: Investigate public records, reviews, and other sources to identify potential reputational risks.
The goal is to make informed decisions about whether to engage or continue working with a vendor.
3. Risk Mitigation and Contractual Safeguards
Once risks are identified, the next step is to address and mitigate them through strategic measures and strong contractual agreements.
- Mitigation Strategies
- Limit Access: Restrict vendor access to only the data and systems necessary for their tasks.
- Implement Controls: Require vendors to adopt your organisation’s security protocols, such as multi-factor authentication or encryption.
- Robust Contracts
Contracts are a vital tool in setting clear expectations and safeguarding against risks. Key provisions should include:- Data Protection Obligations: Specify how data should be handled, stored, and protected.
- Service Level Agreements (SLAs): Define performance expectations and metrics to measure vendor effectiveness.
- Audit and Termination Clauses: Allow for periodic audits and outline conditions under which the contract may be terminated.
Clear and enforceable contracts create accountability and reduce ambiguity in vendor relationships.
4. Ongoing Monitoring and Governance
Risk management does not end with onboarding. Continuous oversight is necessary to adapt to changing circumstances and maintain compliance.
- Continuous Monitoring
Utilise automated tools and technology to monitor vendor performance, detect anomalies, and identify emerging risks in real time. - Regular Reviews
Schedule periodic evaluations to reassess vendor compliance with contractual obligations and evolving regulations. This ensures that the relationship remains aligned with organisational goals. - Vendor Governance Committees
Establish a governance structure to oversee TPRM activities. These committees should include representatives from relevant departments, such as legal, IT, and procurement, ensuring a holistic approach to third-party risk management.
5. Incident Response and Contingency Planning
Despite the best preventive measures, incidents involving third parties can still occur. Preparedness is essential to minimise impact.
- Incident Response Frameworks
Develop clear procedures for managing third-party-related incidents, such as data breaches or service disruptions. These frameworks should include communication protocols, roles, and responsibilities to ensure a swift and effective response. - Business Continuity Plans
Work closely with vendors to establish contingency plans that maintain service continuity during emergencies. Regularly test these plans through simulated scenarios to identify and address any gaps.
6. Offboarding and Exit Strategies
The end of a vendor relationship can pose risks if not managed carefully. A structured offboarding process is essential to protect organisational assets and data.
- Controlled Offboarding
Ensure a secure transition by:- Revoking vendor access to systems and data.
- Retrieving or securely disposing of sensitive information handled by the vendor.
- Lessons Learned
Conduct a post-offboarding review to evaluate the relationship and identify areas for improvement in future engagements. This reflective process can uncover valuable insights to refine your TPRM methodology.
The components outlined above form the foundation of a comprehensive TPRM methodology. By systematically addressing each stage of the vendor lifecycle, organisations can effectively mitigate risks, enhance compliance, and build resilient partnerships. Adopting a proactive and structured approach to third-party risk management not only safeguards the organisation but also demonstrates a commitment to responsible and ethical business practices.
A well-executed TPRM methodology is no longer a luxury—it is a necessity in today’s complex and dynamic business landscape.
Best Practices for Implementing TPRM Methodology
- Integrating TPRM with Enterprise Risk Management (ERM): Align TPRM with your organisation’s broader ERM framework to ensure consistency and comprehensive oversight.
- Investing in Advanced Technologies: Adopt AI-driven tools that enable predictive analytics, risk scoring, and real-time monitoring of vendor activities. These technologies streamline risk identification and enhance decision-making.
- Building a Culture of Risk Awareness: Foster a culture where employees and third-party vendors understand and prioritise risk management. Conduct regular training sessions to reinforce TPRM principles.
- Staying Updated with Regulatory Changes: Maintain awareness of evolving regulatory landscapes and adjust TPRM methodologies to ensure compliance.
- Establishing Clear Communication Channels: Transparent communication between your organisation and vendors promotes trust and ensures that all parties are aligned on risk management goals.
Challenges in TPRM Implementation
Despite its importance, implementing a robust TPRM methodology can be challenging:
- Resource Constraints: Smaller organisations may struggle to allocate the necessary budget and personnel for comprehensive TPRM efforts.
- Complex Vendor Networks: Managing risks across a diverse and extensive vendor base can be overwhelming.
- Dynamic Risk Landscape: Rapidly evolving threats, such as cyberattacks, require constant vigilance and adaptability.
Actionable Insights for Effective Third-Party Risk Management (TPRM)
Implementing an effective Third-Party Risk Management (TPRM) programme requires a thoughtful and strategic approach. While the task may seem daunting, breaking it down into manageable steps and incorporating best practices ensures a smoother and more impactful process. Below are actionable insights that can help organisations implement TPRM effectively, ensuring risks are mitigated and relationships are managed efficiently.
1. Start Small but Scale Strategically
It is neither practical nor resource-efficient to launch a comprehensive TPRM programme covering all vendors simultaneously. Starting with high-risk vendors and scaling the programme gradually is a pragmatic approach that delivers immediate value.
- Focus on High-Risk Vendors First:
Begin by identifying vendors that have the highest potential to impact your organisation’s operations, data security, or compliance. High-risk vendors typically include those with access to critical systems or sensitive data. By addressing these relationships first, you can significantly reduce exposure to the most pressing risks. - Expand to Lower-Risk Vendors Over Time:
Once a robust process is established for high-risk vendors, gradually include medium- and low-risk vendors in your TPRM programme. This phased approach allows for continuous learning and refinement of your processes without overwhelming your resources. - Iterative Process Improvement:
Use insights gained from managing high-risk vendors to refine the methodology and tools before expanding. This ensures that the programme is scalable and adaptable to cover a wider range of vendor relationships effectively.
2. Engage Stakeholders Early
Third-party risk management is not the responsibility of a single department. It requires collaboration across various functions to ensure all aspects of risk are identified, assessed, and managed effectively.
- Involve Cross-Functional Teams:
Engage key stakeholders such as legal, IT, procurement, compliance, and operations early in the process. Each team brings unique insights and expertise:- Legal can ensure contracts include robust risk mitigation clauses.
- IT can evaluate vendors’ cybersecurity measures.
- Procurement can identify critical vendors and oversee contract negotiations.
- Develop a Unified Framework:
Collaboration ensures that the TPRM framework aligns with organisational objectives and regulatory requirements. A unified approach prevents silos and ensures risks are managed holistically. - Create a Communication Plan:
Establish clear communication channels and regular updates for all stakeholders. This keeps everyone informed and engaged throughout the TPRM lifecycle, from vendor selection to ongoing monitoring.
3. Leverage External Expertise
Managing third-party risks internally can be challenging, especially for organisations with limited resources or expertise. Engaging external specialists can provide invaluable support and enhance the effectiveness of your TPRM programme.
- Partner with Risk Management Firms:
External firms specialising in TPRM can offer expertise in areas such as vendor assessments, compliance monitoring, and incident response planning. These firms often have access to advanced tools and databases that streamline risk identification and mitigation. - Access to Industry Best Practices:
Risk management firms are well-versed in industry standards and regulations. Their expertise ensures that your TPRM practices remain compliant with evolving laws and align with best practices. - Customised Support:
Many third-party risk management firms provide tailored solutions based on the specific needs of your organisation. This can include customised risk assessment frameworks, training for internal teams, or ongoing monitoring services. - Cost-Efficiency for Smaller Organisations:
For smaller organisations, building an in-house TPRM capability can be cost-prohibitive. Leveraging external expertise offers a cost-effective alternative, providing access to high-quality risk management without the need for significant investment in internal resources.
Implementing These TPRM Insights in Practice
To effectively integrate these insights into your TPRM efforts, consider the following steps:
- Conduct a Risk Prioritisation Exercise: Identify and categorise vendors based on their risk profiles to determine where to focus initial efforts.
- Establish a Steering Committee: Form a cross-functional committee to oversee the development and implementation of the TPRM programme.
- Evaluate External Partners: Research and engage credible third-party risk management firms with proven track records in your industry.
- Pilot and Scale: Begin with a pilot programme for a subset of high-risk vendors, assess its success, and then expand the scope based on findings.
- Monitor and Refine: Continuously assess the effectiveness of your TPRM practices, incorporating feedback from stakeholders and leveraging insights from external partners.
Effective TPRM implementation requires a combination of strategic focus, cross-functional collaboration, and external expertise. By starting small, engaging stakeholders early, and leveraging the support of specialists, organisations can build a scalable and impactful TPRM programme. This approach not only safeguards the organisation against potential risks but also enhances vendor relationships and operational resilience. Adopting these actionable insights ensures that TPRM becomes an integral part of your organisation’s broader risk management strategy.
Third-party risk management (TPRM) is a critical discipline in today’s interconnected business landscape, addressing the challenges posed by external vendor relationships. By implementing a comprehensive third-party risk management framework, organisations can systematically identify, assess, and mitigate risks, ensuring business resilience and regulatory compliance. From creating robust third-party risk management policies to deploying effective third-party risk management software, a proactive approach safeguards against operational disruptions, data breaches, and reputational damage.
Integrated third-party risk management solutions are essential for streamlining processes across the third-party risk management lifecycle. Organisations can benefit from advanced third-party risk management platforms and tools that enable real-time monitoring, detailed risk assessments, and efficient vendor management. These tools enhance the effectiveness of third-party risk management programs and ensure alignment with industry best practices.
For businesses seeking to strengthen their third-party risk management process, the adoption of third-party risk management services from specialised vendors can provide expert insights and scalable support. Such services often include tailored risk assessments, policy development, and ongoing monitoring to address unique organisational needs. Careers in third-party risk management are also on the rise, as organisations recognise the importance of dedicated professionals to manage and mitigate vendor risks.
The adoption of comprehensive third-party risk management solutions, frameworks, and tools ensures that organisations remain resilient and secure in an era of increasing third-party dependencies. By prioritising integrated strategies and leveraging advanced platforms, businesses can successfully navigate the complexities of third-party relationships and position themselves for long-term success.
How can Neotas TPRM solutions help?
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM). In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Moreover, Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
If you’re curious about whether our third-party risk management solutions and services align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
Third Party Risk Management (TPRM) Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Vendor Due Diligence
- Open Source Intelligence (OSINT)
- Introducing the Neotas Enhanced Due Diligence Platform
Poplar Articles on TPRM Methodology:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Vendor Due Diligence Checklist
- Supply Chain Risk Management
- Due Diligence Explained: Types, Checklist, Process, Reports
- Third Party Risk Management (TPRM) Lifecycle
- Third Party Risk Management (TPRM) Framework
- Third Party Risk Management (TPRM) Software
FAQs on TPRM Methodology
What is TPRM methodology?
TPRM methodology refers to the structured process of identifying, assessing, mitigating, and monitoring risks associated with third-party relationships. It aims to protect organisations from potential threats arising from third-party vendors, including cybersecurity risks, compliance issues, operational disruptions, and reputational damage. A well-designed methodology integrates risk management into the vendor lifecycle for comprehensive oversight.
Why is TPRM important in modern businesses?
TPRM is vital as organisations increasingly depend on third parties for critical functions. Without proper risk management, vendors can introduce vulnerabilities, including data breaches and regulatory non-compliance. TPRM helps organisations maintain operational resilience, protect sensitive data, and meet regulatory obligations while fostering trust with stakeholders and customers.
What are the key objectives of TPRM?
The objectives of TPRM include:
- Safeguarding sensitive data and systems from third-party risks.
- Ensuring compliance with regulatory standards.
- Reducing operational disruptions caused by vendor failures.
- Enhancing overall governance of third-party relationships.
- Strengthening vendor accountability and fostering trust.
What are the five phases of third-party risk management?
The five phases of TPRM are:
- Identification: Cataloguing all third-party relationships.
- Assessment: Evaluating vendor risks through due diligence and risk profiling.
- Mitigation: Addressing risks with controls and contractual safeguards.
- Monitoring: Continuously overseeing vendor performance and compliance.
- Offboarding: Securely ending vendor relationships while safeguarding organisational assets.
What risks are addressed by TPRM methodology?
TPRM methodology addresses multiple risks, including:
- Cybersecurity Risks: Data breaches and unauthorised access.
- Compliance Risks: Non-adherence to legal and regulatory requirements.
- Operational Risks: Vendor disruptions impacting business continuity.
- Reputational Risks: Negative public perception due to vendor misconduct.
What is the TPRM lifecycle methodology?
The TPRM lifecycle methodology encompasses all stages of managing third-party relationships, including:
- Pre-engagement risk assessments.
- Contract negotiation and vendor onboarding.
- Continuous monitoring and risk reassessments.
- Incident management and remediation.
- Offboarding with secure termination processes.
Who is responsible for TPRM within an organisation?
Responsibility for TPRM typically falls on risk management, compliance, procurement, and IT departments. A cross-functional governance committee often oversees TPRM to ensure alignment across the organisation. Senior management plays a key role in setting policies, while operational teams execute the TPRM strategy.
What are TPRM policies and procedures?
TPRM policies and procedures outline an organisation’s approach to managing third-party risks. They include guidelines for vendor risk assessments, compliance requirements, incident response, contract terms, and continuous monitoring. These policies ensure consistency, compliance, and accountability across all vendor relationships.
What are the three P’s of total risk management?
The three P’s of total risk management are:
- Processes: Establishing structured procedures for identifying and mitigating risks.
- People: Assigning responsibilities and fostering a risk-aware culture.
- Policies: Defining rules and frameworks to guide risk management efforts.
What is RCSA methodology in risk management?
RCSA (Risk Control Self-Assessment) is a methodology that allows organisations to identify and assess risks within their operations. It involves documenting risks, evaluating control effectiveness, and assigning ownership for remediation. In TPRM, RCSA is often applied to evaluate vendor-related risks systematically.
How does TPRM methodology support regulatory compliance?
TPRM methodology ensures compliance by embedding regulatory requirements into vendor assessments and monitoring processes. This includes verifying adherence to laws such as GDPR, FCA guidelines, and industry-specific standards. Effective TPRM reduces the risk of fines and reputational damage caused by vendor non-compliance.
What are the common challenges in implementing TPRM methodology?
Challenges include:
- Managing risks across a large vendor ecosystem.
- Limited resources for comprehensive risk assessments.
- Vendor resistance to stringent security requirements.
- Adapting to rapidly changing regulatory and technological landscapes.
Overcoming these requires strategic prioritisation, stakeholder collaboration, and the use of automated tools.
How does technology enhance TPRM methodology?
Technology improves TPRM by automating risk assessments, real-time monitoring, and compliance tracking. Tools like artificial intelligence (AI) and machine learning provide predictive analytics to detect emerging risks, while integrated platforms offer dashboards for streamlined vendor management and reporting.
What is the role of due diligence in TPRM?
Due diligence is a cornerstone of TPRM, involving detailed evaluations of vendor capabilities, compliance, and security measures. It ensures that vendors meet organisational standards before onboarding. For high-risk vendors, enhanced due diligence includes cybersecurity audits, financial reviews, and regulatory compliance checks.
How can organisations improve their TPRM methodology?
Organisations can enhance their TPRM methodology by:
- Adopting advanced technologies for automation and analytics.
- Regularly updating policies to reflect evolving risks and regulations.
- Conducting continuous training for employees and vendors.
- Engaging external experts for specialised assessments.
- Integrating TPRM into their broader enterprise risk management strategy.




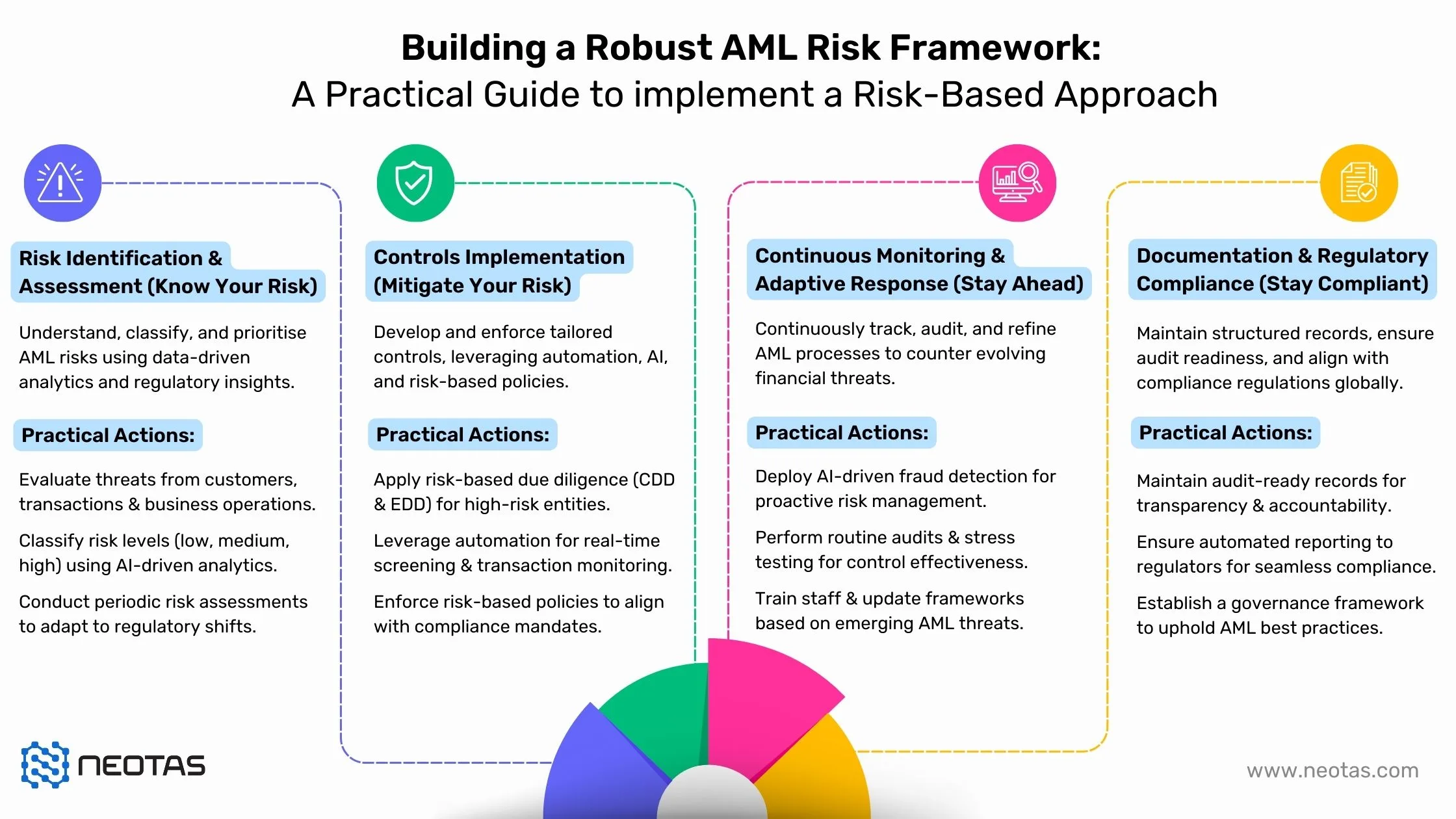
 Identify high-risk customers, transactions, and business relationships.
Identify high-risk customers, transactions, and business relationships. Strengthen regulatory compliance.
Strengthen regulatory compliance.